Status: Alert not Alarmed
Australia and New Zealand have both experienced cyber-attacks as results of their on-going support for Ukraine and for their relationships with Israel. Geopolitically driven hacktivist activity continues to be an active part of the threat landscape.
The Australian Government was also involved in the revealing of LockbitSupp, one of the most prominent operators of Lockbit ransomware and one of the most prolific cyber criminals since at least 2019.
There continues to be fall-out from the ZircoDATA BlackBasta ransomware attack. If you would like more context around this attack, see the report I put together about the possible initial access vector. Monash Health is the most notable victim currently disclosed that was impacted as a third-party of the initial attacks.
I did see some media reporting, that suggested their were two threat groups involved, this is not the case - it was actually the initial access broker who then sold on access to BlackBasta. Also, I would really like to drive-home that opportunistic and financially motivated threat actors, such as Black Basta are rarely targeting organizations with state based goals. It is incredibly unlikely that the Russian government was involved in the targeting of ZircoData with ransomware.
It is important that we highlight that point as too often analysts and the media are keen to leverage that narrative when it simply isn’t the case, just because ransomware groups may operate out of Eastern Europe does not mean their every action is orchestrated by a state.
Pro-Russian Hacktivists Declare Campaign Against Australia.
This is worth its own section as the main hacktivist group behind the current attacks has very strong links according to Mandiant to Russian state-sponsored group APT44 (Sandworm) making these ironically much more state driven activity then any ransomware attack that any Australian analyst or media outlet has claimed in the past 2 years.
On 10 May, 2024 Cyber Army Russia Reborn and one of their support groups, Hacknet declared a new campaign against Australia. The group conducts DDoS attacks that can last for as long as 30 minutes. Cyber Army of Russia Reborn has also recently been revealed by Mandiant to be heavily linked to APT44 or Sandworm ,a prolific Russian state-sponsored cyber group.
Overall, these attacks have little impact to the websites targeted, with limited periods of unavailability and also the attacks coming often late at night. However, the intent to target Australia as a means to try and influence and shape our geopolitical posturing is worth noting. Geopolitical hacktivist groups, such as the two pro-Russian groups involved in these attacks are keen to draw attention to their activities and disrupt the day-to-day of Australian citizens in hopes of muddying the information environment. In this case they want Australia to stop supporting Ukraine with military aid.
Key Points
This is now the most sustained pro-Russian hacktivist campaign against Australia ever. With 10 websites targeted with DDoS attacks.
It appears each day two websites are targeted and they range from strategic targets, such as Ports and government websites to small business websites.
This is consistent with regular activities of pro-Russian groups.
This campaign may continue for the next 24-48 hours.
Cyber Army Russia Reborn has conducted targeting of Operational Technology in the past, so being aware of the groups activity in Australia is important.
It is unclear if APT44 (Sandworm) is involved with this campaign, but it might be worth cyber defenders being aware of the latest activity, TTPs and technical indicators of APT44 just in case.
The Targets
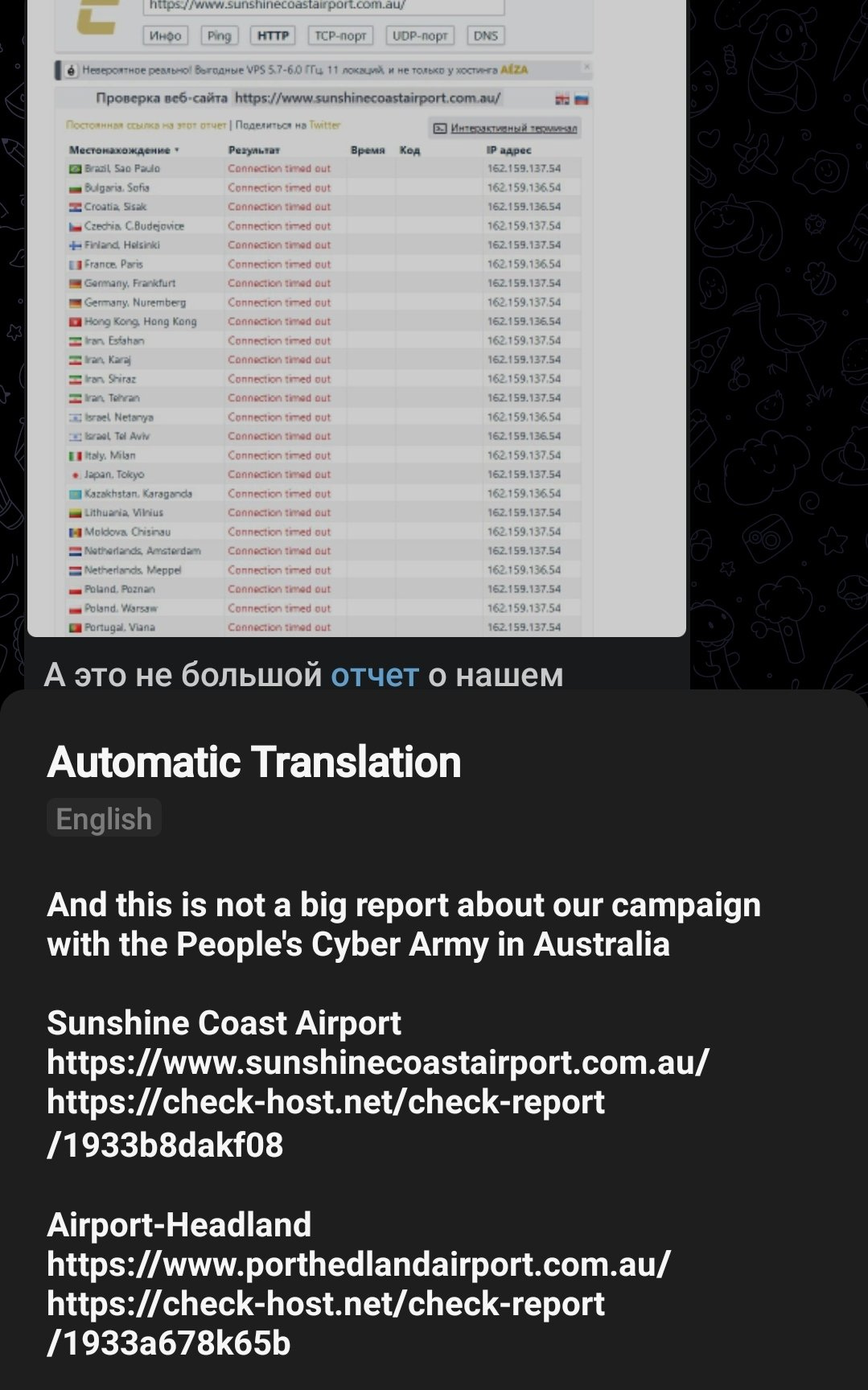
10 May - Sunshine Coast Airport and Port Hedland Airport.
This attack was carried out by Cyber Army Russia Reborn and Hacknet. These DDoS attacks were successful for a limited period of time.
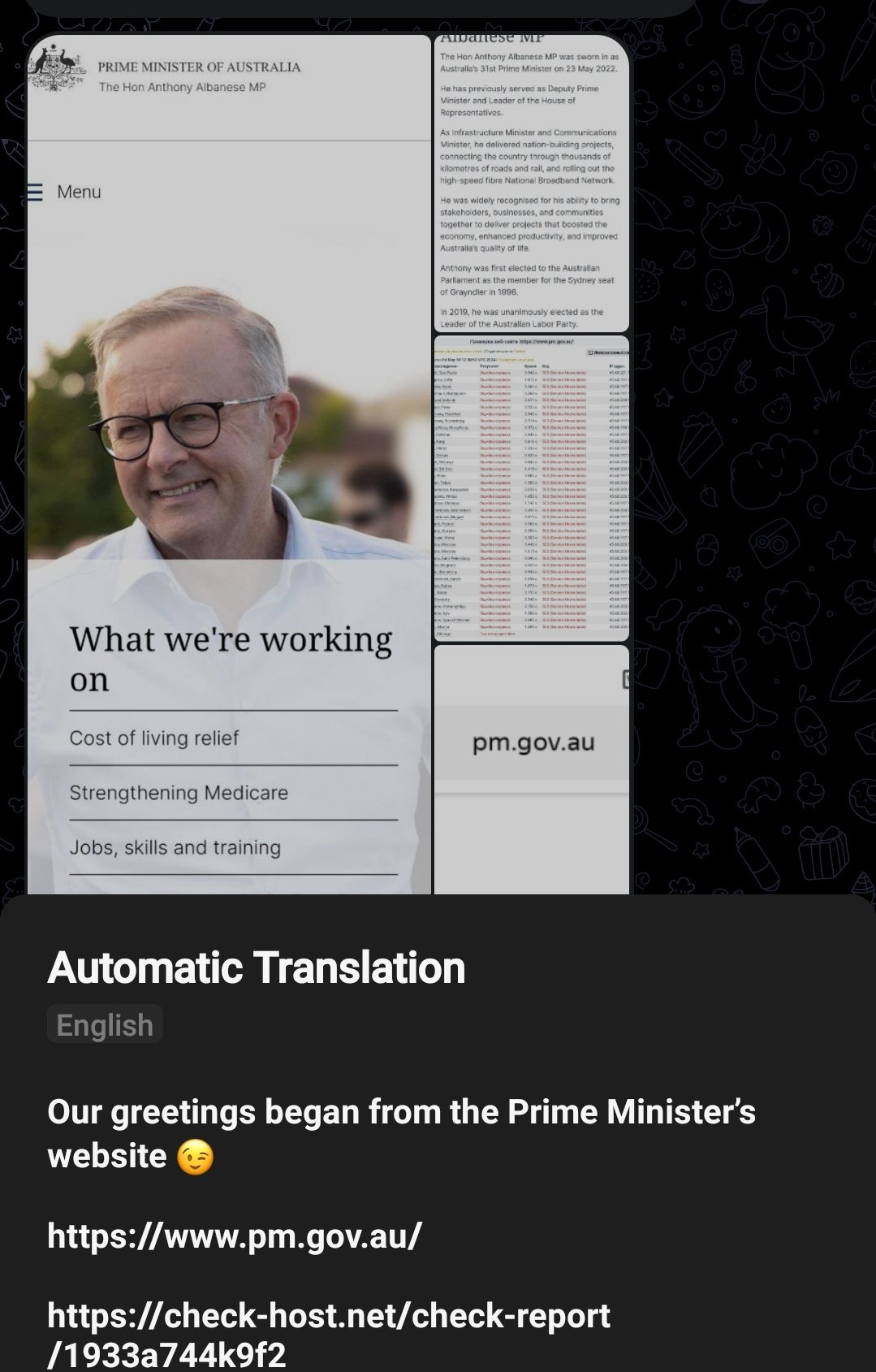
10 May - Prime Minister’s official website. This attack was carried out by Cyber Army Russia Reborn and Hacknet. It was successful for a limited amount of time. This DDoS attack also signifies one of the only times a Russian state linked group has impacted an Australian government website in direct attacks.
11 May - Port of Melbourne was targeted with DDoS by Cyber Army Russia Reborn and Hacknet. I could not confirm if this was successful. (Port of Melbourne website was taken down by Anonymous Sudan in early 2023)
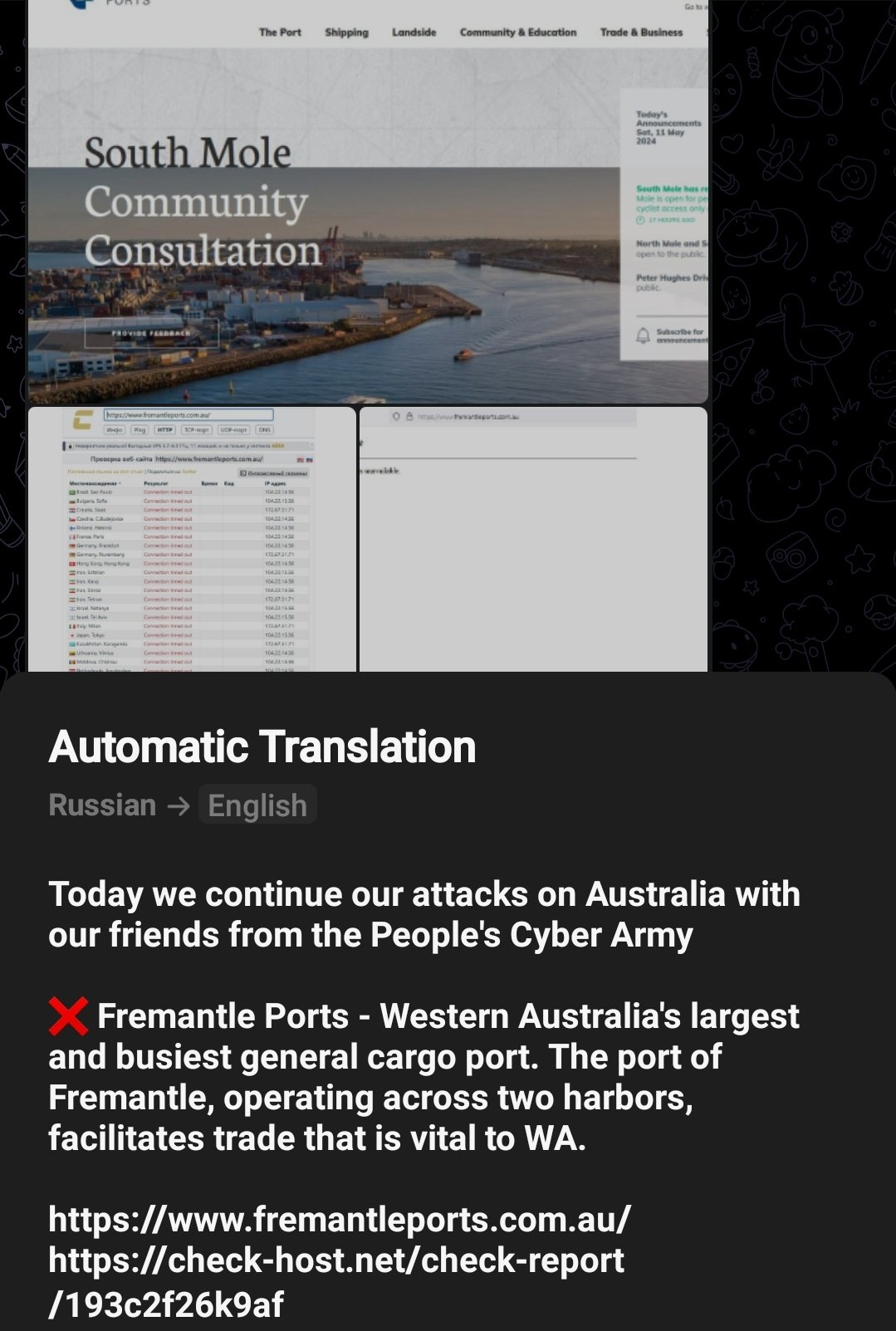
11 May - Fremantle Port website was targeted with DDoS - the same groups as previous. Unclear if this was successful or not, but the intent to target Ports should be of note to Australians.
May 11 - Australian Geospatial Intelligence Organization, website for a tool was targeted. Unconfirmed is success.
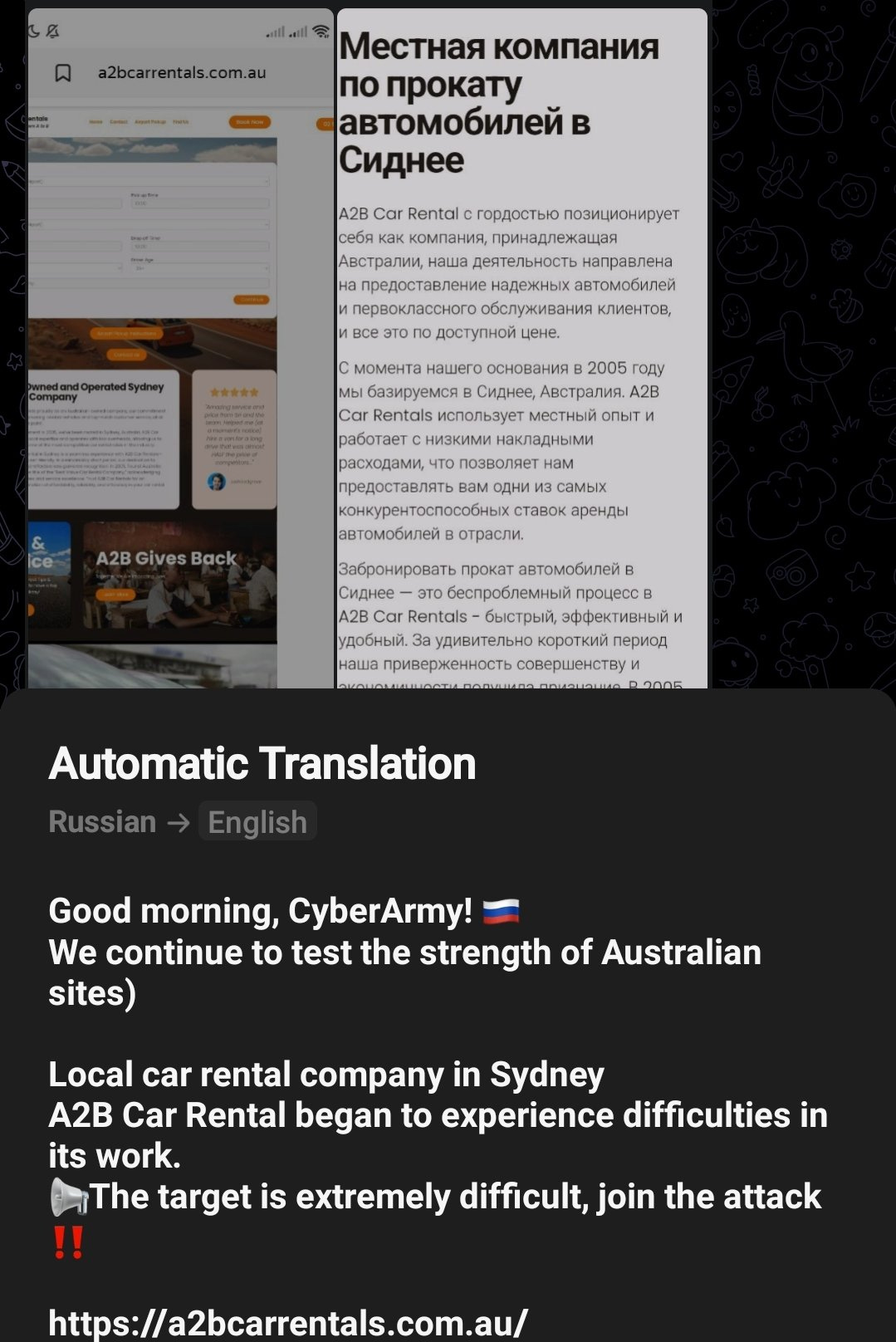
May 12 - a2b car rentals website was targeted by Cyber Army Russia Reborn and Hacknet. Unconfirmed is success or not.
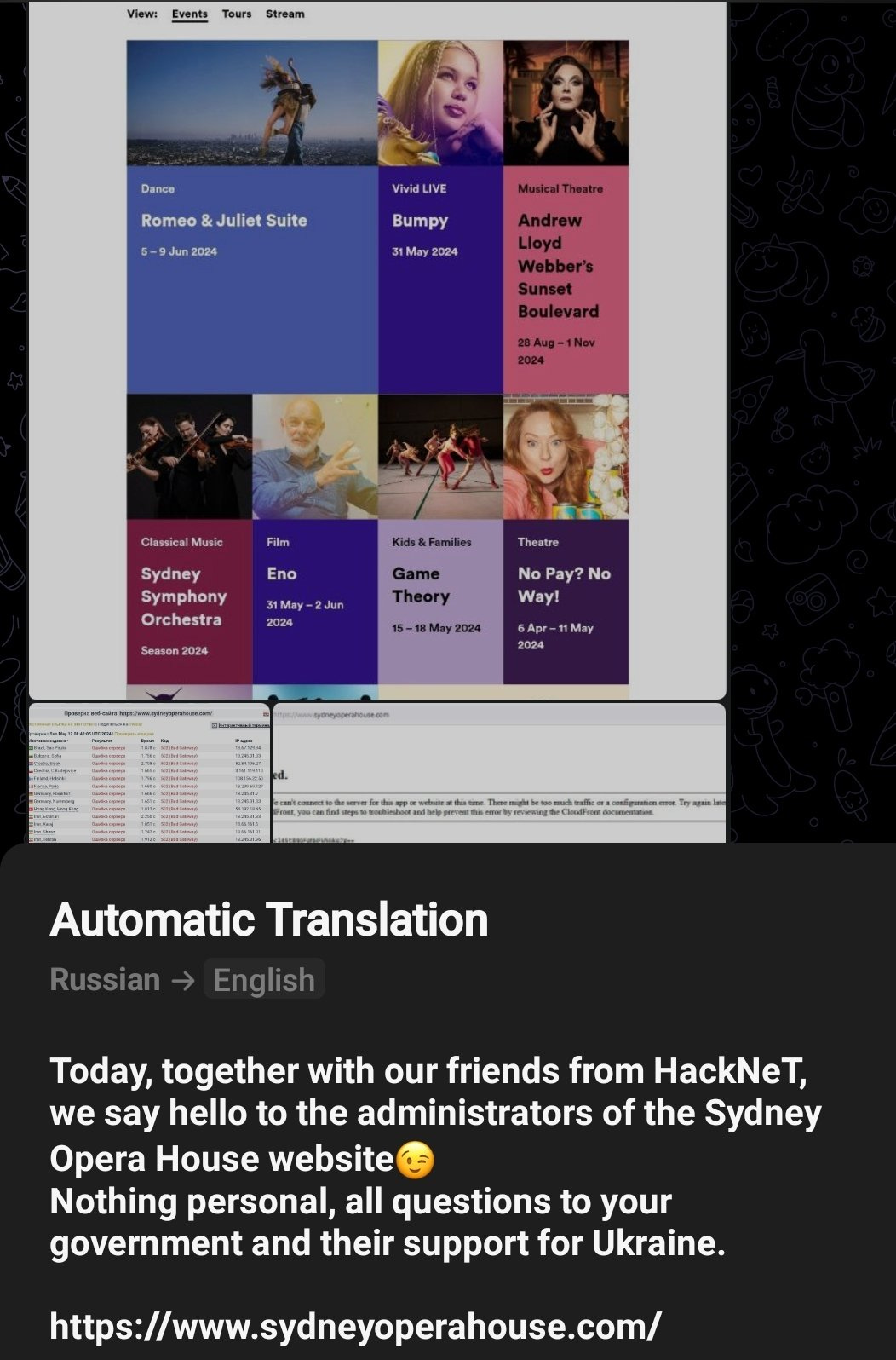
May 12 - Sydney Opera House website was targeted, unclear if successful.
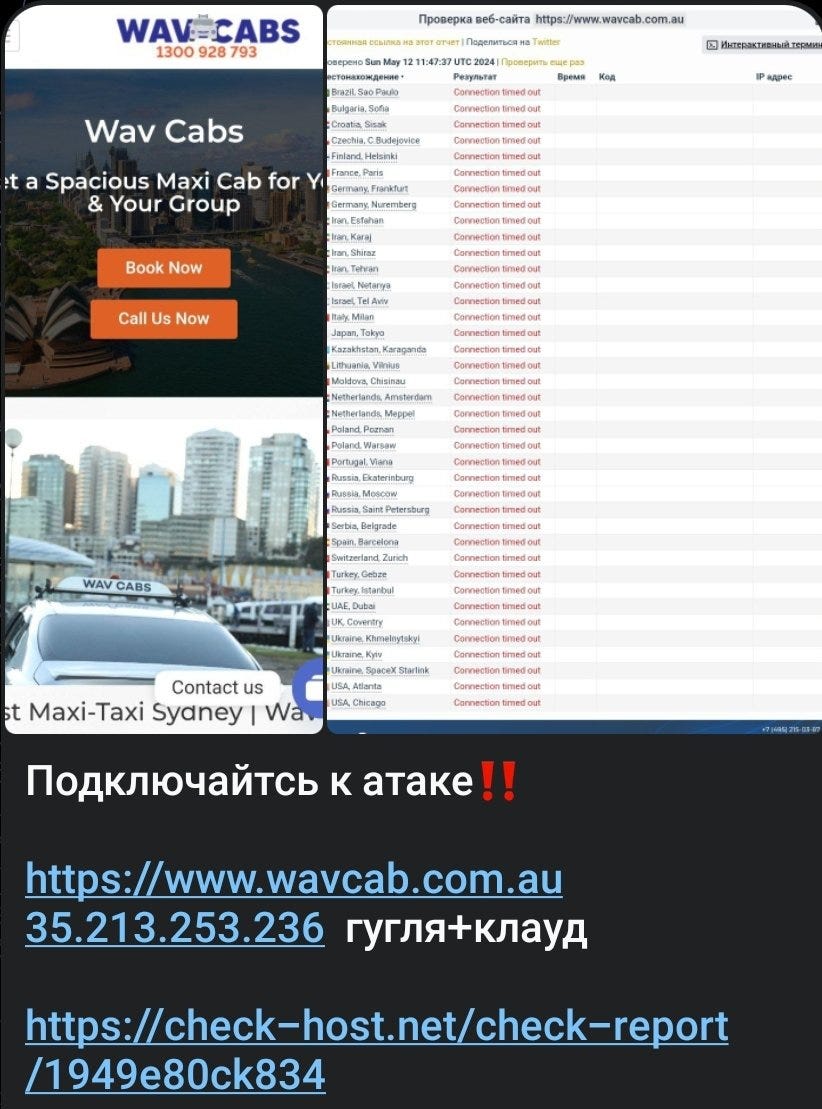
May 13 - Wavcabs website was targeted. Unclear if successful.
May 13 - AuditCo website was targeted. Unclear if successful or not.
Hacktivist Activity - 10 Victims 6 Australian and 4 New Zealand
4 May - Australia
4-Exploitation targeted three Australian websites.
4 May - Australia
4-Exploitation claimed access to the Job Training Institute of Australia.
5 May - Australia
Ethersec claimed a deface attack against an Australian organization. It is possible that the group has impacted AquaCell an Australian company, but not Telstra.
6 May - Australia
Aligator Black hat claimed to ‘hack’ a Telstra control system.
8 May - New Zealand
Rippersec claimed a defacement of Crystal Glass in New Zealand, the group thought it was a United States company.
11 May - New Zealand
Ethersec claimed to have access to a New Zealand company, but could not provide any evidence at time of reporting.
11 May - New Zealand
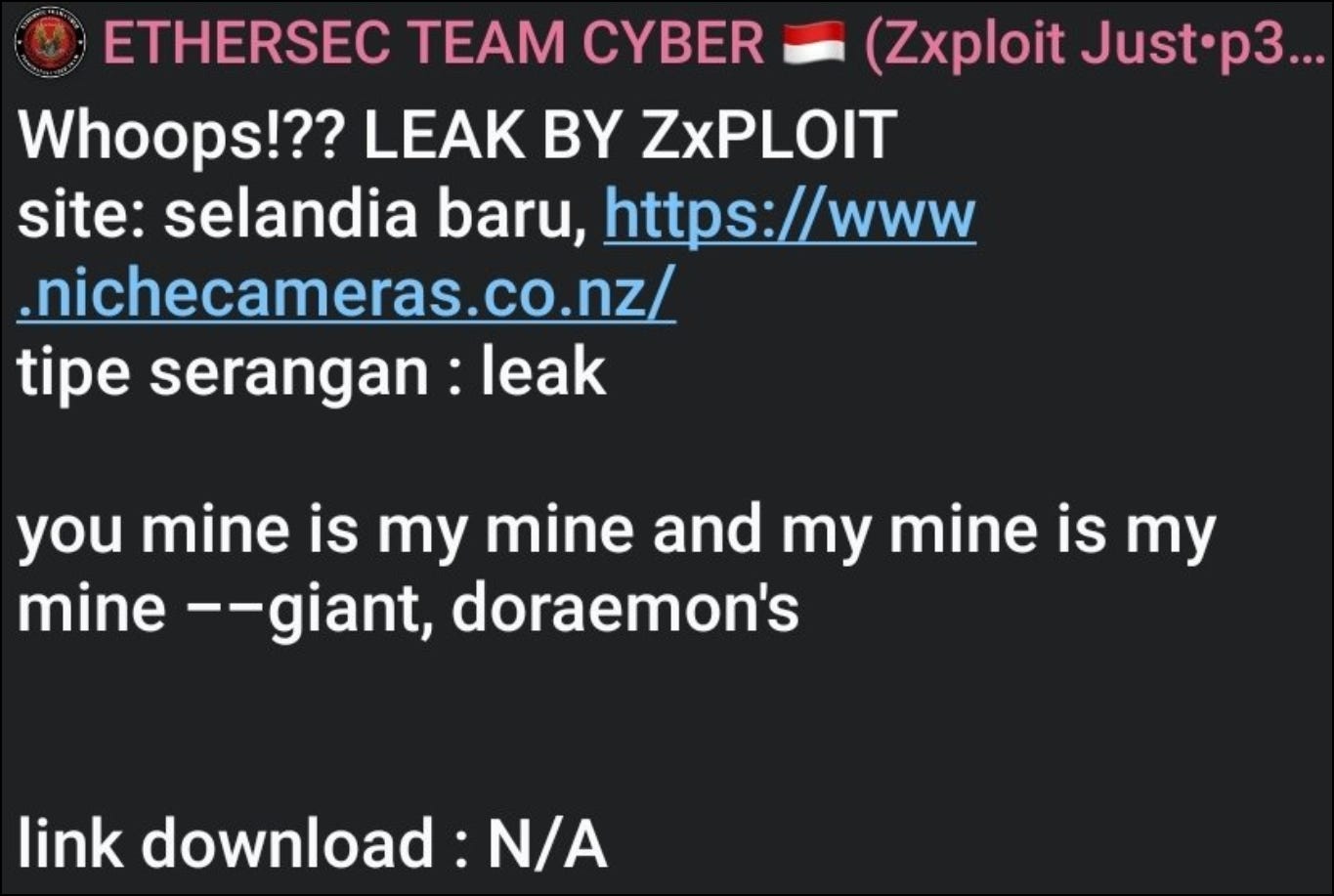
Ethersec claimed to have access to Niche Cameras in New Zealand, but could not provide evidence at time of reporting.
12 May - New Zealand
Ethersec defaced a New Zealand organization.
The latest Pro-Russian hacktivist campaign has been added to the above section.
Ransomware - 0 Victims
In a first there were no Australian or New Zealand organizations added to ransomware leak sites during the reporting period.
Underground posts/mentions of Note
Nothing significant to Report
For regular updates or for more information: https://twitter.com/Cyberknow20