Status: Alert not Alarmed
Despite continued hacktivist activity, the overshadow in Australian cyberspace came on Saturday morning, 11 November when the Home Affairs minister announced the cyber incident at DP World Australia which is currently impacting port operations across 4 of Australia’s largest ports. We continue to track and monitor these activities and provide regular updates on X(Twitter).
DP World Australia
On 10 November, the AFR broke the news that DP World Australia, the second largest port operator in Australia, had suspended operations in its Sydney, Melbourne, Brisbane and Fremantle ports after it detected unauthorized access to its network Friday afternoon. At the time of writing, media outlets are reporting that the ports remain closed as the company investigates.

Late on Saturday afternoon, Darren Goldie, Australia’s new National Cyber Security Coordinator, posted that the National Coordination Mechanism (NCM) had been stood up in response to the incident, and that interruptions to port operations are expected to continue “for a number of days”. This incident will be the National Office of Cyber Security (NOCS) and Goldie’s first real test for coordinating a whole of government response to major cyber incidents since their commencement earlier this year.
Though this is a developing story, we have a few preliminary thoughts. The targeting of shipping ports by threat actors is not unheard of, with the most recent example being the 4 July ransomware attack on the Japanese Port of Nagoya by an unknown LockBit affiliate. The attack reportedly disrupted the port’s communication systems, forcing the port’s operator to suspend its operations for two days, as well as shutting down its network to contain the infection. Though it is unclear whether the incident affecting DP World is ransomware, the response from both port operators appears much the same. As was observed during the Colonial Pipeline ransomware attack by the REvil gang, an observed intrusion can activate emergency response procedures that can have cascading effects on business operations, including the suspension of critical services.
The incident affecting DP World Australia will already go down as the largest disruptive cyber attack on critical infrastructure in our nation’s history, but how disruptive to our economy and society it will actually be remains to be seen. The speed and efficacy of the response to this incident will be the primary differentiator, and pressure will be on how well DP World and the Australian Government can coordinate to safely resume operations. The importance of recovering from this incident quickly is further underlined by planned industrial action set to commence on 14 November that will see import and export shipping operations disrupted at the Sydney, Melbourne and Brisbane terminals.
Hacktivist Activity - All Hacktivist Activity for this period was anti-Israel driven. 20 Victims targeted.
October 31
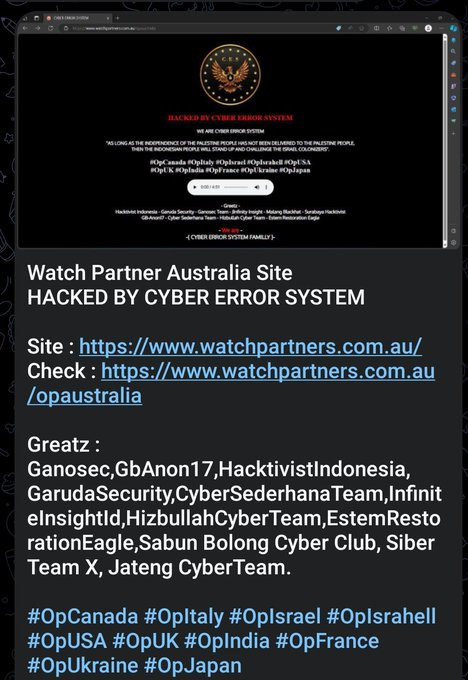
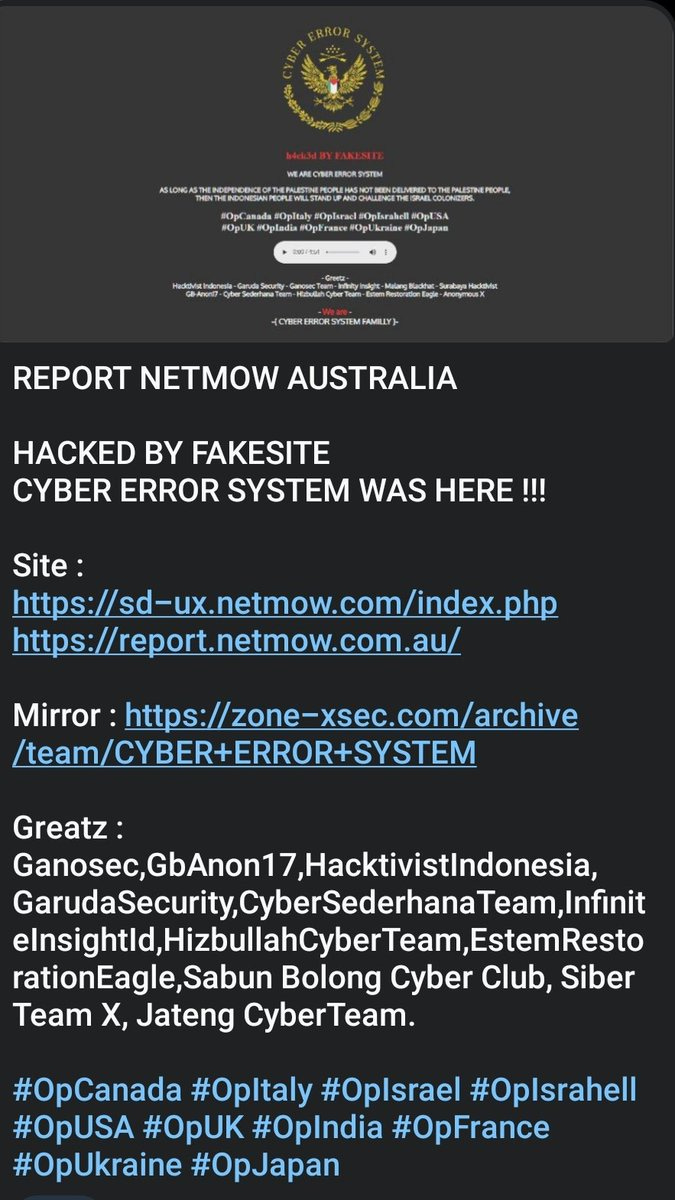
Cyber Error System defaced an Australian watch making company.
October 31
The Camp 22 attempted a DDoS attack on the defence ministries of 13 countries. The Australia attempt was unsuccessful.
November 1
Esteem Restoration Eagle and its collective members claimed a defacement of an investment company.
November 3
Esteem Restoration Eagle defaced the website of a small outdoor furniture store in Australia.
November 3
Esteem Restoration Eagle allegedly defaced a renewable energy company in Australia.
November 3
Esteem Restoration Eagle allegedly defaced the Early Childhood Teachers association and another small Australian business.
November 4
Cyber Error System defaced an Australian website.
November 4
Garuda Security defaced two Australian trades services website
November 5
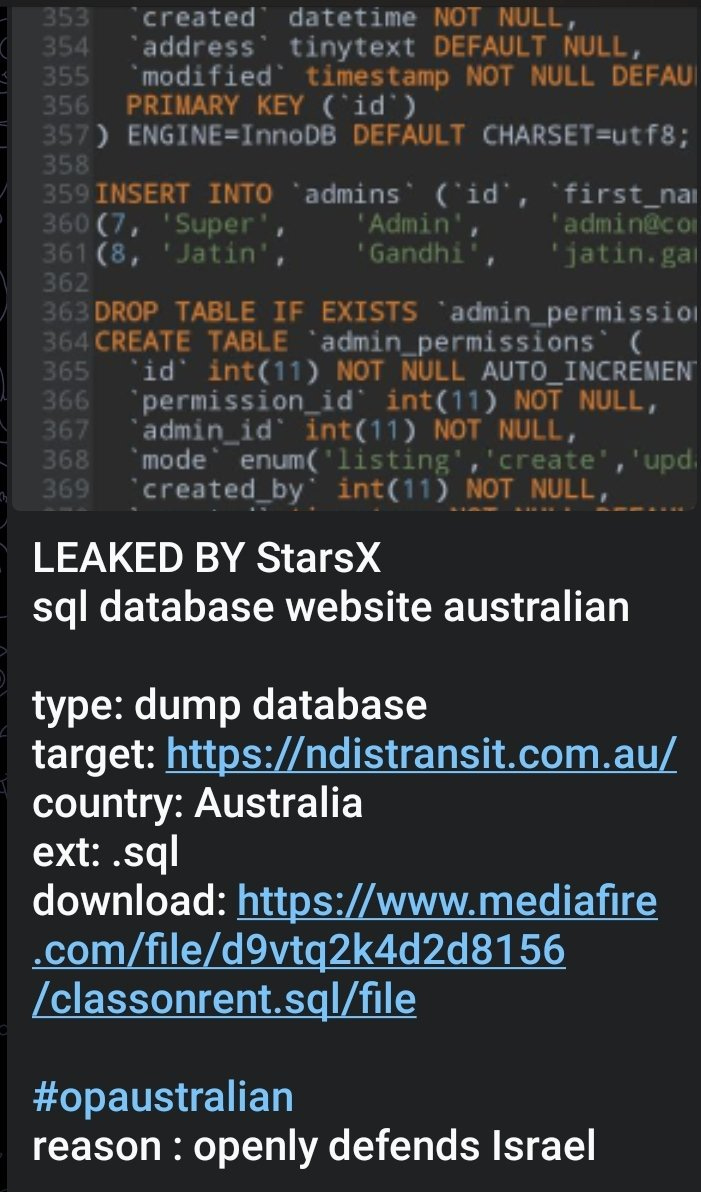
StarsX Team claims the leak of an SQL database from an Australian website.
November 6
Garuda Security claimed they would target what they believed to be a Queensland government website, despite the site being a .com.au site note .gov.au. No evidence they actually targeted this site.
November 6
Infinite Insight.ID defaced an Australian small business services company.
November 7
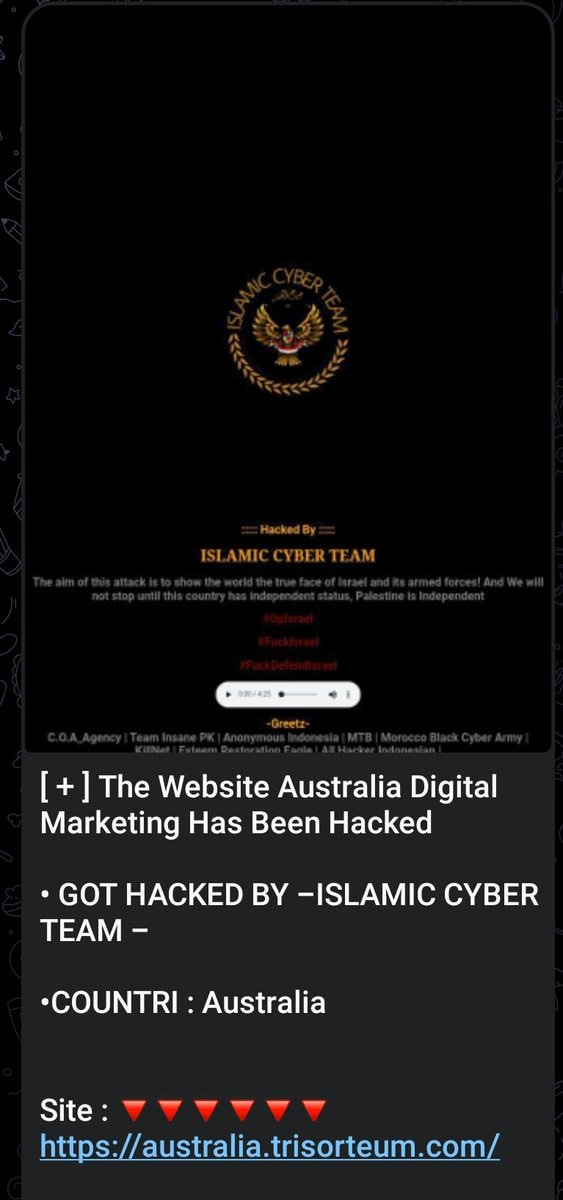
Islamic Cyber Team Indonesia defaced an Australian digital marketing website.
November 8
This is such an interesting attack and great example that this will be expanded into a larger blog.
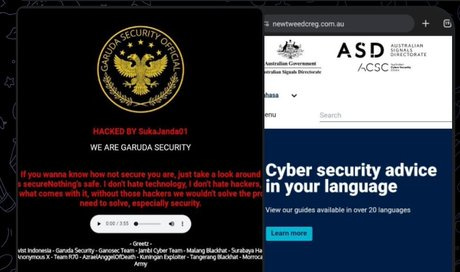
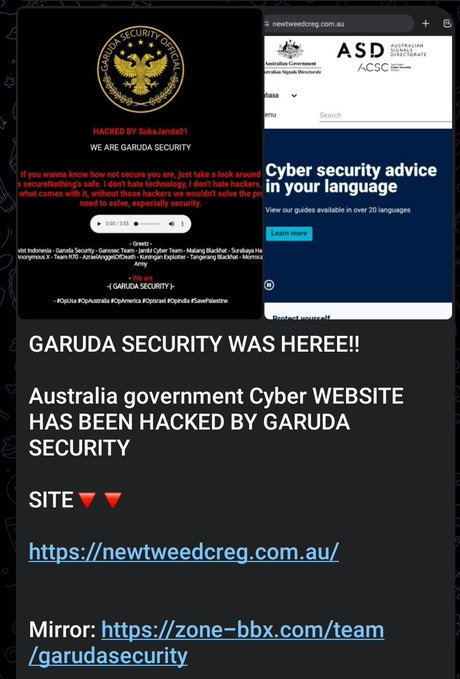
Garuda Security claimed to deface the website of the Australian Signals Directorate (ASD) instead it appears they have defaced a real estate company from the Tweed Coast. This is a great example of the fake claims made by these groups.
November 8
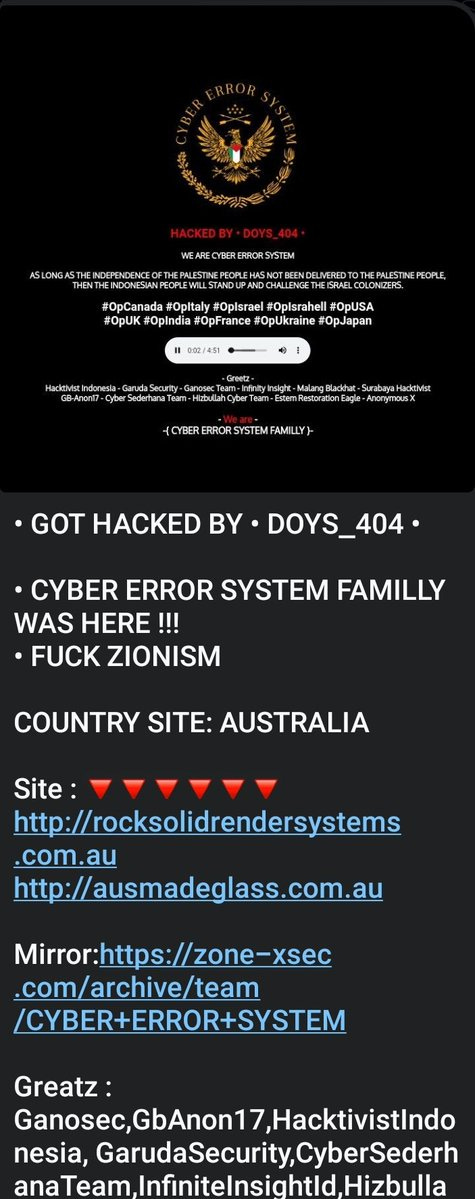
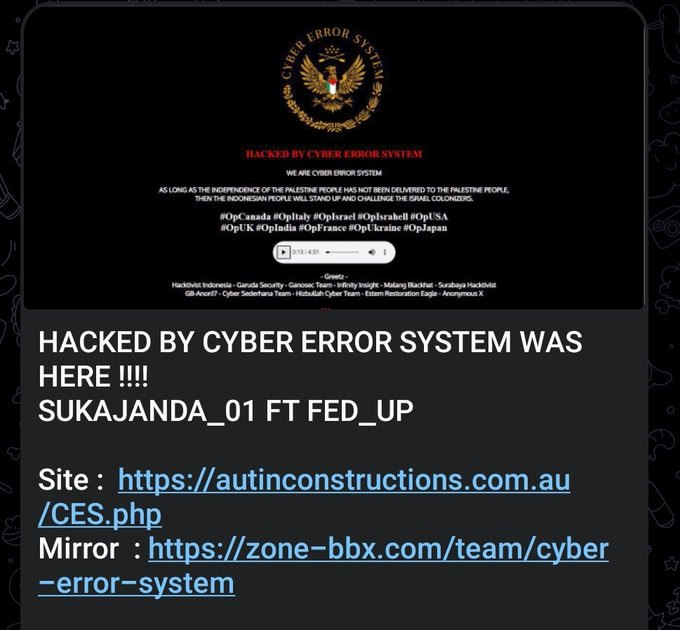
Cyber Error System defaced an Australian construction company website.
November 9
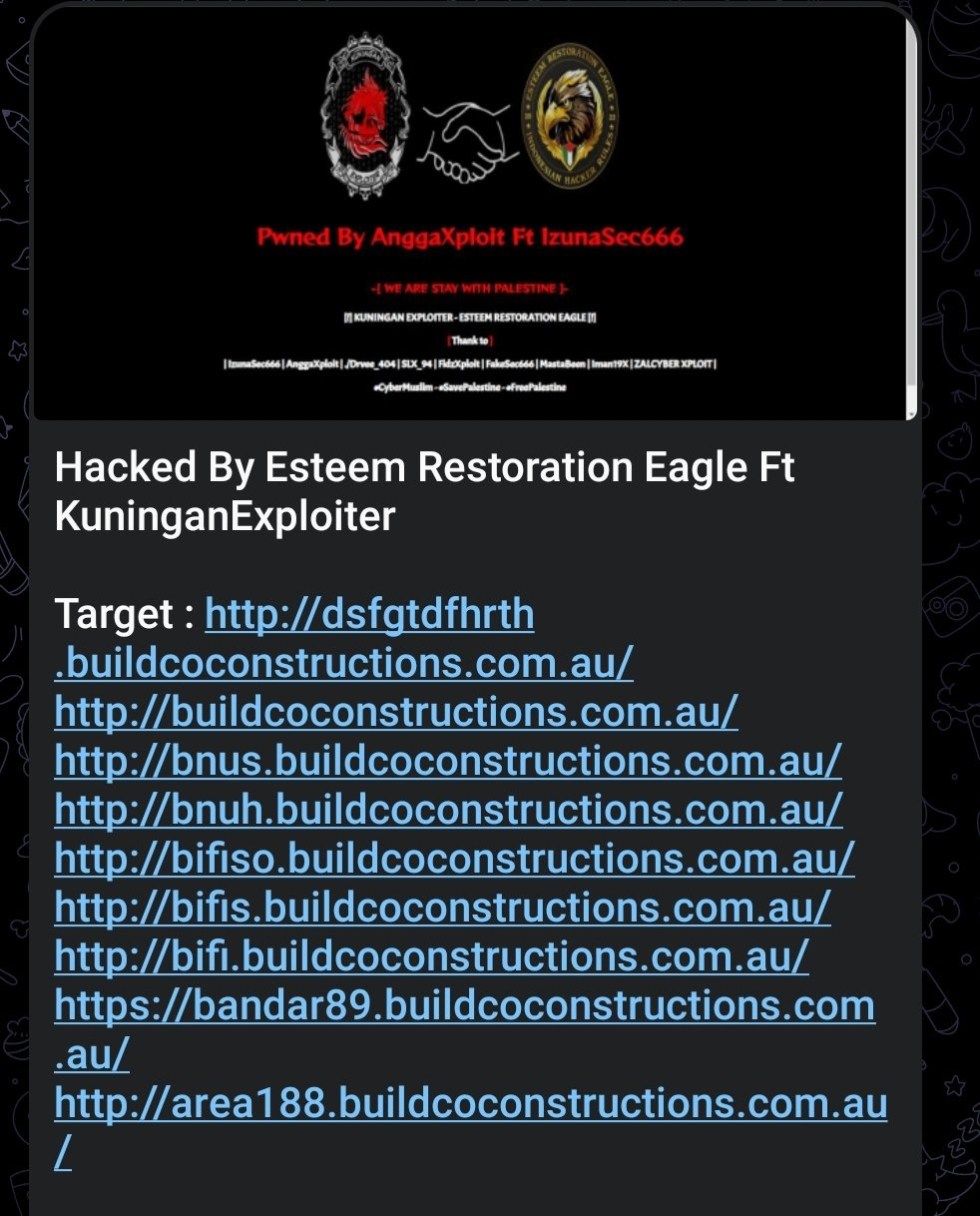
Esteem Restoration Eagle and KuninganExploiter defaced multiple subdomains of an Australian building company.
November 9
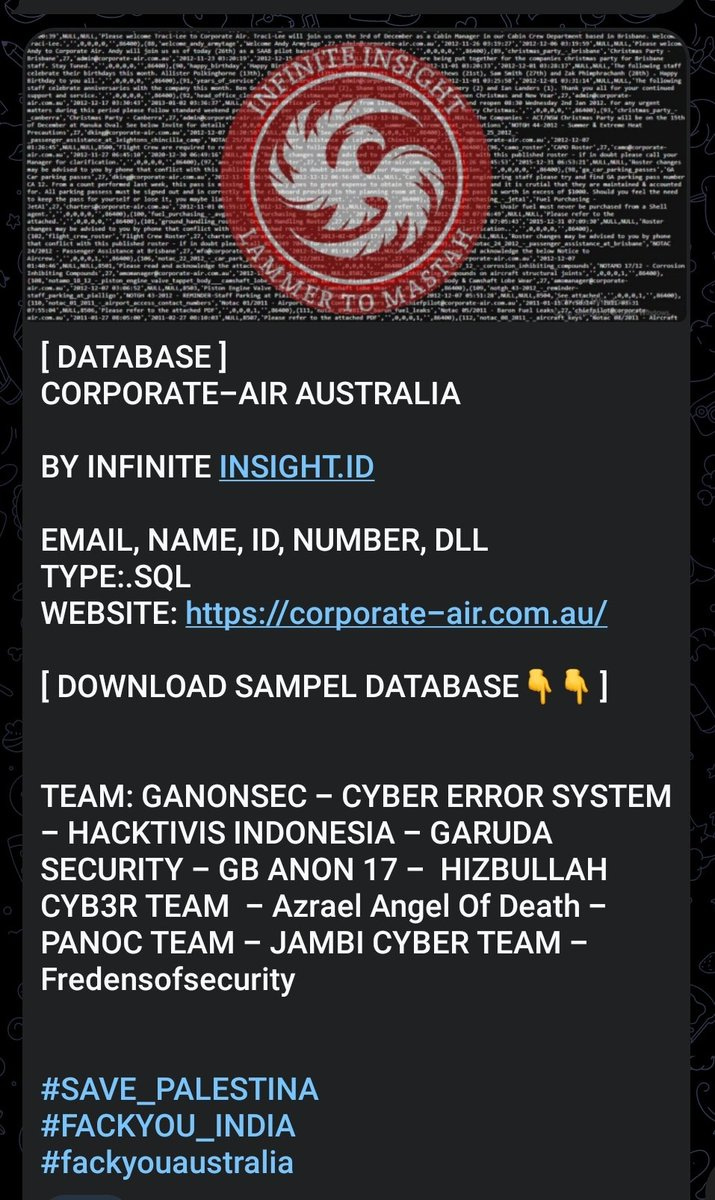
Infinite Insight.ID claimed to breach and leak a database from Corporate-Air Australia which provides flight services for mine workers across Australia.
November 10
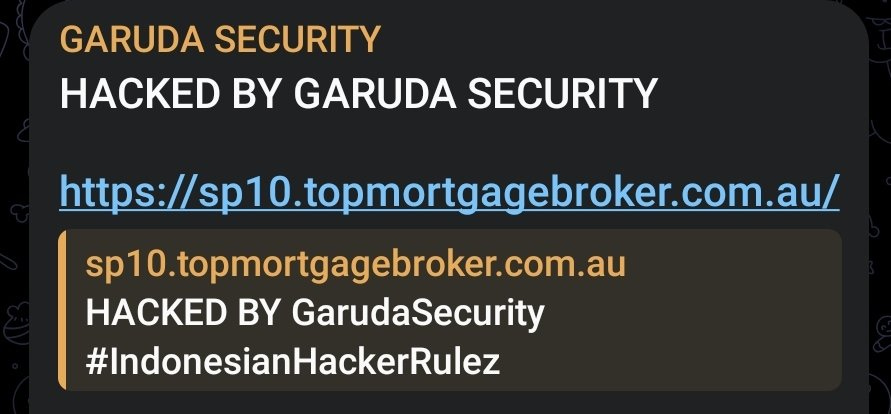
Garuda Security claimed to deface an Australian mortgage broker website.
November 13
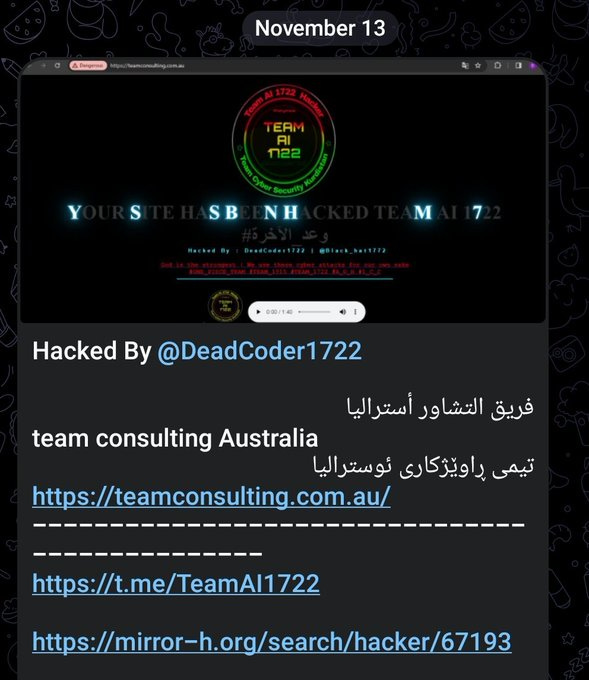
Team1722 posted a defacement of an Australian consulting company.
Ransomware - 3 Victims
October 31
Lockbit ransomware gang posted Frontline Equipment Maintenance PTY to their leaksite.
October 31
Lockbit ransomware gang posted SmartUI Group to their leaksite.
October 31
BianLian extortion gang posted Auswide Services to their leaksite.
November 9
Noescape ransomware gang posted Ezi Floor Product to their leaksite.
Underground posts/mentions of note
October 31 to November 12
There were three posts of Australian organization network access during the last two weeks.
The third post does provide the ‘domain(.)com(.)au’ network as systeminfo - noting that threat actors don’t normally share the name of the victim network it could be an error.
At time of this report all these posts are still up for sale.
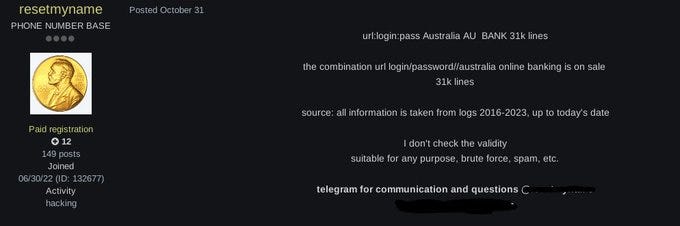
October 31
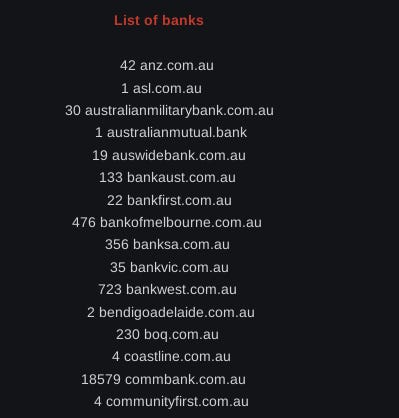
A user on Exploit forum posted a collated list of Australian banking logs, dating from 2016 till 2023. At time of posting they have not sold the list - this is likely because the shelf life for log files can be quite short, especially when attempting to leverage cookies.
They claim to have a diverse list from several banking organizations in Australia. Note that password change policies and multi-factor authentication can provide a good baseline protection from compromised accounts stolen from infostealers. However, the broader challenge is the removal of the infostealer malware from infected devices.
November 4
A user on breachforums claimed to have the database belonging to the Australian exporters.
November 9
A user on Exploit Forum claims to be able to conduct sim swaps in Australia. This user has been on and off active on the forum and across other platforms and repeatedly gets called out for being a possible scam.
If you have any additional insights or questions please reach out to: