Australia Cyber Update #9 (First for 2024)
11 December to 10 January (2024)
Status: Alert not Alarmed
Its 2024 and we are back to keep you across the Australian cyber threat landscape in our fortnightly blogs. Hopefully everyone reading this had some kind of rest, noting that there was plenty of cyber activity in Australia throughout the holiday period.
You will note that even with increased reporting on cyber activity by the media over the period there is no need to raise the status level. What we continue to see is opportunistic targeting by hacktivist and cyber criminal groups. (Reminder that this is an OSINT report, we have no visibility into more advanced activity often carried out by state-sponsored groups)
Court Services Victoria Ransomware Attack
On 2 January 2024, Court Services Victoria (CSV) issued a statement on their website describing a cyber intrusion that was first detected on 21 December 2023. The intrusion reportedly disrupted CSV’s audio visual technology network and resulted in the potential access of court hearing recordings from several jurisdictions between at least 1 November and 21 December 2023. CSV confirmed that “no other court systems or records, including employee or financial data, were accessed.” In response to the intrusion, the audio visual network was isolated from the rest of CSV’s network and “arrangements” put in place to continue operations across the courts for January cases, which will continue.
Since the statement, media outlets have uncovered additional details of the cyber attack on CSV. An article released by the ABC on 2 January 2024 indicates that the intrusion was financially motivated, with threat actors leaving a ransom note which threatened the leak of stolen data unless a ransom is paid. The article also reveals that a source close to the investigation said CSV had “almost certainly been hit by a Russian phishing attack, using commercial ransomware known as Qilin”. At the time of writing, no additional information corroborating this claim has surfaced.
Network defenders looking to extract intelligence from the cyber attack on CSV would benefit from a quick refresh on the ransomware landscape. Qilin, and many other outfits like it, operate a ransomware-as-a-service (RaaS) model. As a result, the attribution to the Qilin RaaS is ultimately unhelpful, as its many affiliates will have their own favored initial access and intrusion techniques to achieve their goals. Instead, it would be more prudent for defenders to keep track of the common intrusion methods being used by many ransomware affiliates, such as those highlighted in vendor blogs and reports such as Crowdstrike’s October 2023 “How Does Ransomware Spread? 10 Most Common Infection Methods”.
The nature of the alleged stolen data is cause for concern, though those seeking to profit from its theft may find it next to exceedingly difficult to extract a ransom. On one hand, given the right motivation, it is highly likely that a threat actor could extract useful information that would otherwise be struck from a court record such as names and business accounts. With that being said, the value of the alleged stolen data is dependent on the threat actor accurately determining its value. Australian court cases are notoriously long, and laden with legal jargon. A threat actor seeking to evaluate the true value of court case recordings will likely require an advanced understanding of the Australian legal system and thousands of hours to pour through recordings to find interesting or valuable information. In addition, the Australian Government pledged not to pay ransom demands at the Counter Ransomware Initiative (CRI) Summit in San Francisco.
Hacktivist Activity - 34 Victims
This was a busy period for hacktivist activity targeting Australia. The two biggest events that took place were:
Cyber Army Russia Reborn (CARR) - a group associated with Russian intelligence, leaked a database from a Melbourne taxi booking service.
OPAU was launched by Indonesian hacktivists, who claimed that Australia was selling weapons to the West Papua National Liberation Army or KKB.
Cyber Army of Russia Reborn
On 6 January 2024, Cyber Army of Russia Reborn (CARR), a highly active pro-Russian hacktivist group who has strong links to Sandworm, the Russian intelligence hacking group posted its first Australian victim.
CARR posted a database belonging to the ‘Book Taxi Cab Melbourne’ website. The breached data appears to be from the taxi booking company and contains IP addresses and email addresses of customers who have used the website to book taxis in Melbourne.
This is out of character for CARR who largely conducts DDoS attacks against Ukraine along with some European countries. When the group has leaked databases they have often had some strategic importance to Russia and it is likely they have been given to them from Sandworm or APT28 from Russia to leak on their behalf.
This leak at present does not appear to provide any strategic value. CARR has also never mentioned Australia before, making it a curious post by the group. However, we should not ignore the fact that Australian data has been leaked by a Russian government linked group.
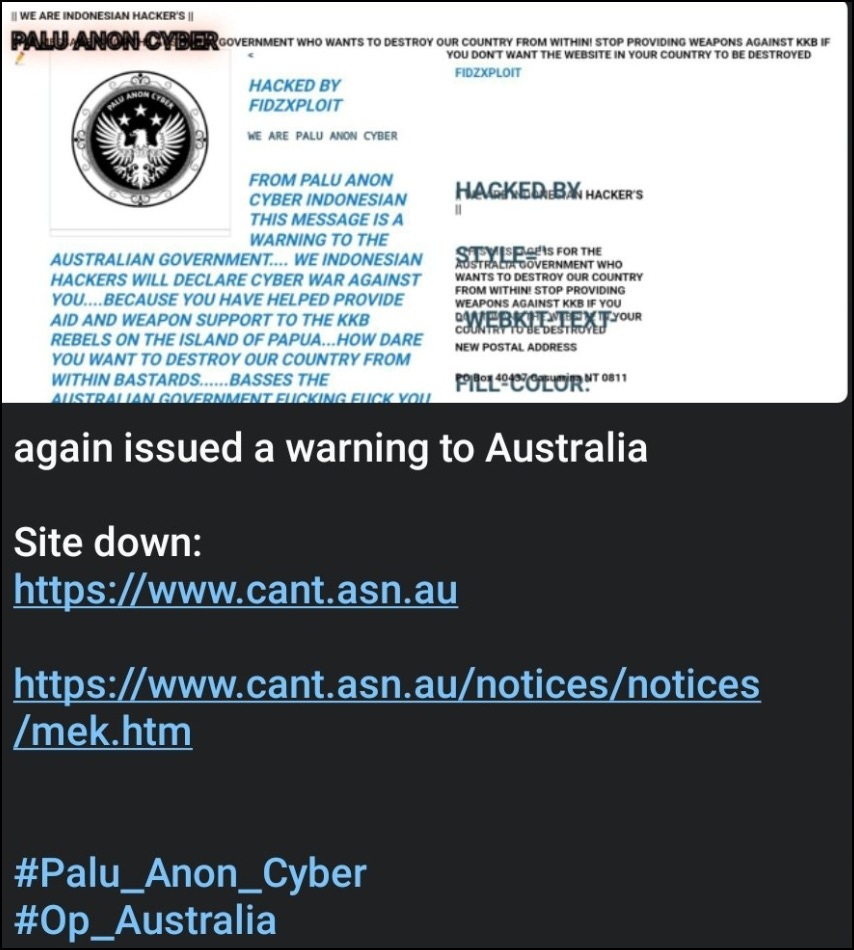
OPAU (OpAustralia)
On 22 December 2023, several Indonesian hacktivist groups started ‘OPAU’ against Australia. The trigger for this campaign was an article from 25 April 2023 that reported on the KKB, who has conducted attacks on the Indonesian military in West Papua. Within the article its reported that the KKB has asked Australia for weapons. (The Australian government has not provided any weapons to the group)
This is another example of how a geopolitical or political flashpoint can trigger hacktivist activity. The following are all the events related to OPAU.
There is little evidence that any of the following attacks had any significant impact.
22 December
Kuningan Exploiter was the first Indonesian hacktivist group to declare they would be attacking Australia.
22 December
Kuningan Exploiter then followed up with screenshots from cameras in Sydney. (It is not difficult or uncommon for hacktivist groups to find open webcams and share these images as a claimed hack.)
22 December
Hacktivist Indonesia returned to activity and joined OPAU - claiming to deface a number of media outlets in Australia. You will note that these are not media outlets, but instead small or medium businesses, the sites that these groups can often deface successfully.
22 December
Team 1722 claimed to target an Australian airport with a deface attack. As above, you will note that ‘syntaxtechs’ is not an Australian airport but instead is a certificate company.
22 December
Cyber Error Team then decided to join the OPAU campaign.
Cyber Error team then conducted several quick attacks:
22 December
Anon Black Flag joined the OPAU campaign - the messages continue to outweigh the capability.
23 December
Anon Black Flag claimed a breach of Australian data, this is often a tactic used by hacktivist groups who find previously exposed data to claim a breach and leak attack.
23 December
Esteem Restoration Eagle joined the OPAU campaign.
23 December
Anon Black Flag successfully defaced Cat association of North Territory - this has been fixed. Intent continues to outweigh capability.
26 December
Team 1722 claimed a deface on an Australian bible study website.
28 December
Islamic Cyber Team joined OPAU with an alleged defacement of a small Australian website.
At this point these groups started to shift back to different targeting and for that reason, we are declaring that OPAU has ended. However, there continued to be other targeting of Australia - largely due to support for Israel.
Other Hacktivist Activity
Due to the volume of activity we will just provide statistics for the Australian organizations targeted during this reporting period.
There were 21 Australian organizations targeted by Hacktivist activity that were separate to attacks reported above.
It was a mix of Deface and DDoS attacks - with at least one database leaked.
All organizations were small or medium Australian businesses.
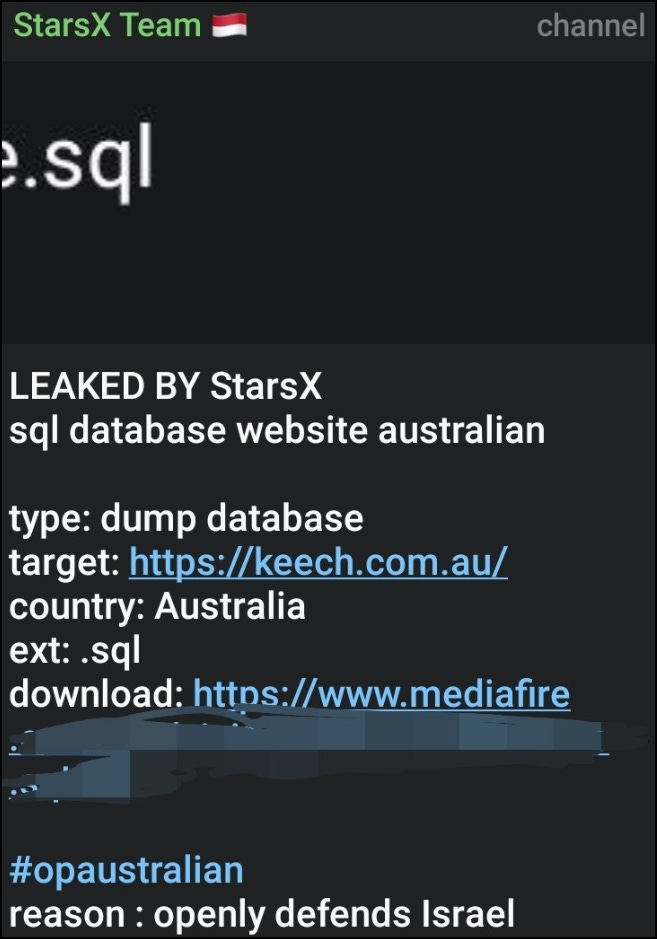
3 January
StarsX Team claimed to have breached keech, an Australian organization. The download did not work when attempting to review the claimed data.
Ransomware - 9 Victims
While recent high-profile ransomware attacks on the Victorian Court System and St Vincent’s Health have controlled the media narrative, an additional number of Australian organizations have been posted to ransomware leak sites.
13 December
8Base ransomware posted Tim Davies Landscaping to its leak site.
15 December
Dragonforce ransomware posted Decina manufacturing to their leak site.
20 December
Dragonforce ransomware posted Yakult to their leak site.
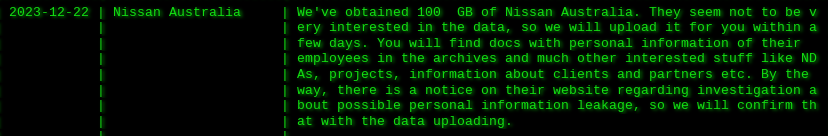
22 December
Akira ransomware posted Nissan Australia to their leak site.
22 December
Lockbit posted Sterling Homes to their leak site.
22 December
Lockbit posted Scientific Motor Body Works to their leak site.
29 December
Cactus ransomware posted Tridon Australia to their leak site.
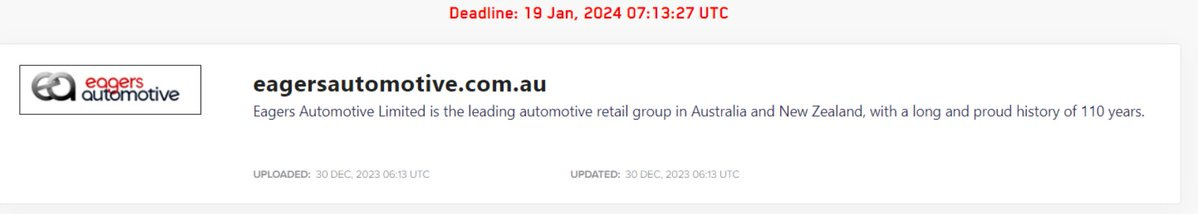
30 December
Lockbit posted Eagers Automotive Limited to their leak site.
9 January
Qilin Ransomware posted Hal Leonard to their leak site.
Underground posts/mentions of note
7 January
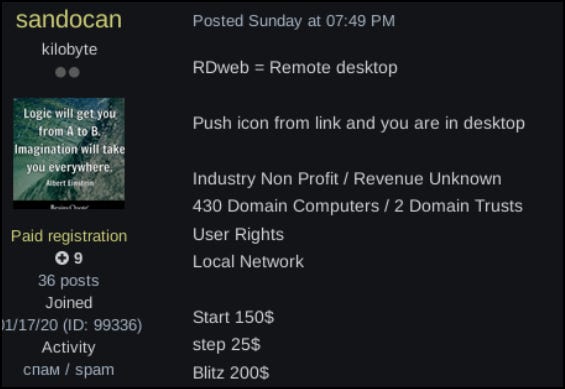
An Initial Access Broker was offering access to an Australian not for profit company. At time of posting this access has not been sold.
If you would like more information on anything within this report please reach out to one of us on X. You will also find regular updates on the Australian threat landscape on our accounts.