TL:DR
Since the unnamed affiliate is not actually REvil or BlogXX I have given them a name for the benefit of reporting: ‘Medibank Marauders’
Medibank has suffered a databreach and is now having its data leaked onto a dark web leak site.
Medibank has been very transparent throughout the breach.
Medibank Marauders have released discussions between themselves and Medibank that provide valuable insights into the intent and operations of the threat group.
This attack was conducted by an unnamed ransomware affiliate and not REvil or BlogXX.
Medibank Marauders will likely continue to leak data on a regular basis in the hope of getting some form of payment from Medibank.
Medibank will not make any payment after public declarations and the involvement of law enforcement.
Threat actor confirmed they did not unleash ransomware on the system, just stole data.
Context
The following report uses the media updates provided by Medibank and the insights from the leaked discussions between the threat actor and Medibank to provide context to the situation.
I am creating this due to a number of questions asked by multiple members in the community, I am simply placing the information that is now publicly accessible into a more understandable format.
The Threat Group
What we knew early on was that this was a ransomware gang, with decent sophistication, however we weren’t clear on which gang it could have been. When the threat was first posted to the old REvil leak site, see image 1 below, now refered to by many researchers as BlogXX, the assumption was that it must be this REvil/BlogXX group. (They stole my meme
However, during the discussion that was leaked by the unnamed affiliate it was revealed that they were using the REvil leak site as one of several options, see image 2 below.
For more detail and information on the history of REvil and reporting on BlogXX see this recent report from Jeremy Kirk - https://www.databreachtoday.com/blogs/who-extorting-australian-health-insurer-medibank-p-3310
Since this unnamed affiliate is unwilling to name themselves and using REvil or BlogXX is inaccurate I feel in the spirit of threat intelligence to give this group a name, that being the ‘Medibank Marauders’ since a marauder is: ‘one who roams from place to place making attacks and raids in search of plunder’ which seems fitting to this situation.
This might be helpful to help clear up confusion as to who was behind the attacks. Or, it is just absolute cringe.
For those wondering, a ransomware affiliate are the actor(s) who normally go onto the victim network to exfil the data and lock the system with ransomware, they traditionally then use ransomware operators such as REvil/Hive/Lockbit who manage the ransomware and the leaksite for a commission. See this report for further details. https://www.crowdstrike.com/cybersecurity-101/ransomware/ransomware-as-a-service-raas/
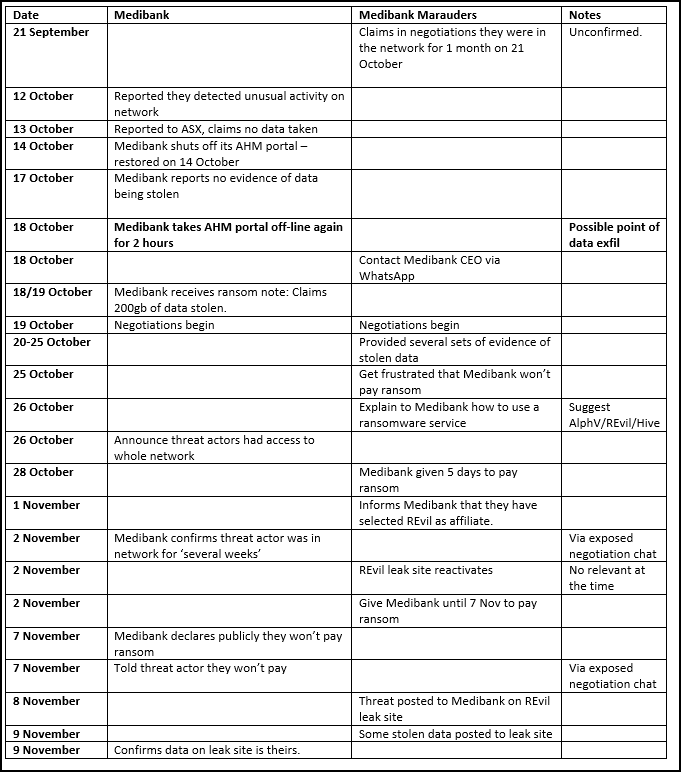
The Timeline
I will apologize in advance, I am not a graphic designer so the timeline does not look like what I had in mind, regardless it does get the point across.
The information below is in the public forum, either from official releases from Medibank or as part of the leaked data posted by Medibank Marauders. However, with the exposed data I have removed anything technical to the attack and instead just provided key dates of events.
There will be large amounts of coverage on Medibank for weeks and my hope is that this timeline will help cut through possible misinformation, it is not intended to glorify the threat group or blame the victim.
Final Thoughts
Did Medibank notify the public too early once they noticed activity in their network?
How long were the Medibank Maruaders in Medibanks network?
This is a significant breach that will impact a large amount of the Australian community, now is the time for the Australian community to be vigilant.