Monitor and Report
The following is a short blog post with some thoughts and insights relating to the Medisecure data breach that was disclosed on the 16th May 2024.
Background
On 16 May 2024, Sky News revealed that an Australian Medical services provider had suffered a data breach. Within hours this was revealed to be Medisecure.
Medisecure was an online pharmaceutical prescriptions provider and up until late 2023 was a providing that service for the Australian government. Since that point the Australian government via the National Cyber Security Advisor has been providing updates related to the incident.
Timeline
The following is a timeline based on the information available as of the 24 may 2024.
May 13, 2024. Medisecure posts a statement onto their website about a data breach. (This appears to have gone unnoticed for several days)
May 15, 2024. Threat actor creates an account on Exploit Forum.
May 16, 2024. Sky news during a morning bulletin reveals that a medical organization in Australia has suffered a ‘nationally significant’ data breach.
May 16, 2024. The Australian National Cyber Security Coordinator declares they were notified on at least the 15 May 2024 that “Yesterday afternoon I was advised by a commercial health information organization that it was the victim of a large-scale ransomware data breach incident.”
May 16, 2024. The Media reveals that the company impacted is Medisecure.
May 17, 2024. Medisecure changes the date of their website statement to the 16 May 2024.
May 23, 2024. A threat actor on an underground forum posts they are selling the Medisecure data for $50,000.
Threat Actor post to Underground Forum.
On May 23, 2024 a threat actor posted the alleged stolen Medisecure data to underground forum, Exploit.
According to the threat actor they have around 6.5TB of data and are demanding a sale price of $50,000 to one customer only. It begs the question, did this threat actor attempt to negotiate with Medisecure? This attempt at a sale of the data does not exhibit the classic extortion tactics we see from ransomware groups and actors.
Analyst Comment:
The threat actor, Ansgar created their account on May 15, 2024 and may well have created it for the sole purpose of attempting to sell the stolen Medisecure data. They have not posted anything else to the forum. (It is possible, with the shut down of Breach forums that this actor has had to pivot to Exploit to try and achieve this sale).
The threat actor, Ansgar has provided several screenshots as evidence.
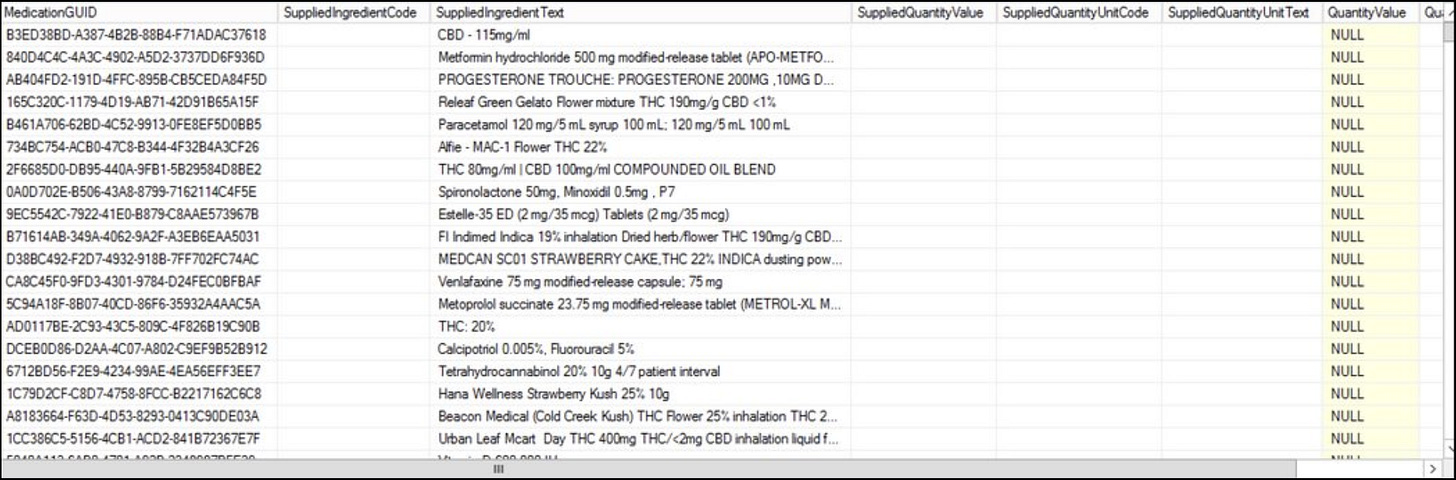
The data does appear to be from prescription for medication.
It also includes a list of Australian pharmacies with approval numbers. These screenshots do suggest this is Australian medical script data.
Confirmation It is legitimate?
Other than the data within the screenshots that looks legitimate we have another indicator which provides us with possible confirmation it is legitimate.
At the bottom of the screenshot files we see the following information.
You will see that the name Paul is present, doing a quick search and there was at one point in time a Paul who worked at Medisecure. (I have redacted additional information)
This makes it highly likely that the threat actor does indeed have the Medisecure data and is looking to sell it.
Thoughts
It is interesting that despite this being a declared ransomware incident by the National Cyber Security Coordinator on 16 May, 2024.
That instead of the expected post on a data leak site run by one of the Ransomware gangs we have a possible single threat actor posting the data for sale on Exploit forum. An actor who made the account close to the time when the data was likely stolen.
This suggests this is a threat actor without infrastructure, where as, if they were operating within a ransomware system they would have negotiation support and a data leak site to post a threat to the victim.
It appears from the limited information that this is not a traditional ransomware extortion shakedown and it begs to wonder if there was any negotiation or extorting attempt between the threat actor and Medisecure.
It is possible that this threat actor may have needed to find an alternative forum to post this data after the shut-down of Breach Forums. With is shut-down they may have pivoted to Exploit to try and sell the data.
A good take-away for Australian’s from this incident is to appreciate that the cyber threat landscape is diverse and groups and actors can impact businesses regardless of their capability, organization or structure.
For regular updates on Australian related cyber activity or all things hacktivism - https://x.com/Cyberknow20