This blog will provide insights into an ongoing Mygov email campaign against Australians.
TL:DR
There is an ongoing Mygov themed phishing email campaign targeting Australians. The attempted phishing emails look like official Mygov email notifications.
This type of activity is not uncommon, but during a period of heightened public awareness around the government, such as our Federal election, the risk of impact to targets is increased.
Recommendations:
Change passwords associated with any data breach.
Get multifactor authentication on accounts where the provider allows it.
Don’t reuse passwords - A password locker might be a good option.
Email Exposed in Data Breach becomes an avenue of Cyber Attacks
I have worked hard over the years to try and protect my main email account - which I like to call my personal critical infrastructure. The reason? This is my main email for bill and financial correspondence and is also used to access my Cloud storage. Unfortunately this email was eventually exposed in a data breach (Thanks Taylor Swift).
What happened to my email?
In October 2024 my critical infrastructure email address had some suspicion actions towards, outlined below. While I had not believed my email had been compromised before - I did note that the timing of the attempted attacks were within several days of the Ticketek data breach being posted to Breachforums. I cross-referenced and noted that my email had been ‘pwned’ on the HaveIbeenpwned site from the Ticketek breach.
What has happened to my email since it was exposed in a data breach?
It has had over six months of sporadic brute force attempts to login using a password.
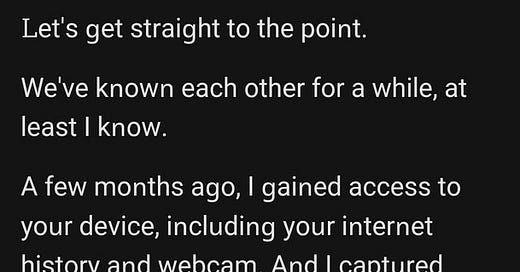
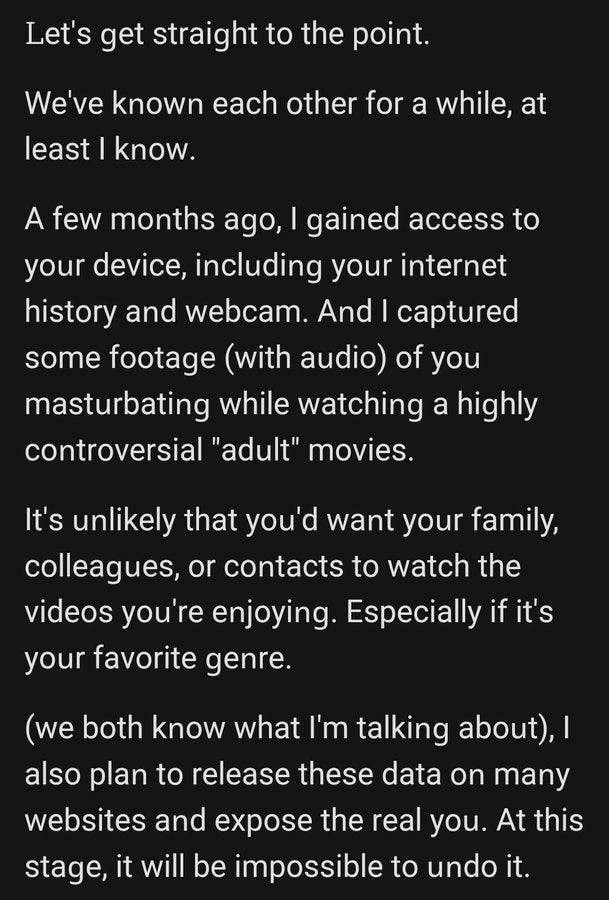
I have had two sextortion emails attempting to illicit an extortion payment.
I have had a series of myGov scam emails.
How I have I ‘fought back’ or held the defensive line?
I changed my email password (noting it was different to any associated with Ticketek)
I checked and changed if I had used my Ticketek or email passwords for anything else (in case they have that password)
I already have but still maintain Multi-Factor Authentication (MFA) on the email account (I use it on every account that will allow MFA) - I use Microsoft authenticator for this email address - it means if my email was exposed then any attacker would also need my mobile device to access a login code.
I report the emails as phishing - this helps Outlook provide better phishing protections which is why all the emails are sent to my junk inbox to start with.
I am sharing this information to improve awareness.
In October 2024 I posted the following to my X account.
There is a scam currently going around - while not unique, it is peddling the - 'ransomware on your system' - 'we also have videos of you watching bad movies' It is still dangerous - I believe it is linked to the Ticketek breach from May 2024. Why do I think that? I received one of these sextortion/scam emails on an email account that has only been breached in the Ticketek breach - the scam email also included my date of birth and full name, both in the Ticketek breach - while not definitive I am confident this might be the source of the scam campaign. If you were involved in the Ticketek breach, stay vigilant, and remember they are trying to evoke a response from you by using personal details.
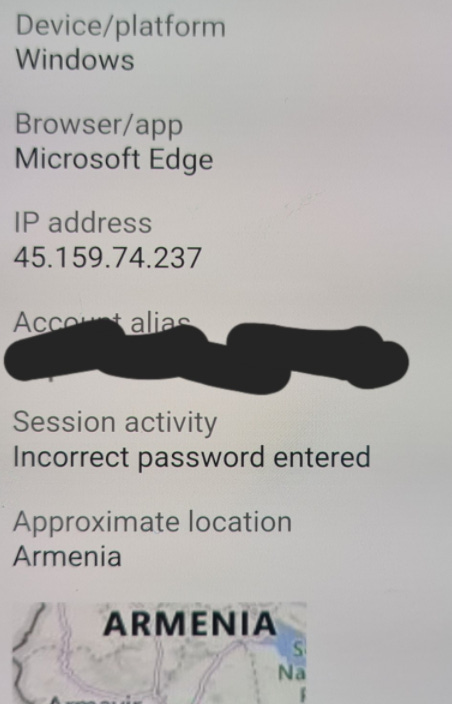
Further to this , the same email account has had 3 failed login attempts in the past two weeks. All blocked due to MFA and password less login settings. 4 October - attempted login 18 October - two attempted logins. All this activity has taken place after the Ticketek database was posted to BreachForums on 28 September. I have not received any correspondence from Ticketek, but I am very confident this is now the source - this is super frustrating as I have attempted to protect this email from these issues. I have also checked the bitcoin address linked to the scam email, and sadly, two victims have paid the ransom of $2000 USD. I am thankful I am aware enough and use things such as MFA, but unfortunately I was not aware my email had been compromised without any correspondence from Ticketek - since it was over 17 millions impacted the likelihood of them all having MFA isn't super high.
This campaign of attempting to brute force my account has continued and in the final two weeks of April 2025 there were over 50 attempts to get into my email account.
Mygov Phishing Campaign
Starting in March 2025 I was exposed to a Mygov phishing campaign that has persisted until the end of April (so far). These campaigns are not new, but could be having more success during March and April 2025 as the Federal Election creates more interest in the government and government services.
Below are the first wave of emails I received (this is the same email that was exposed in the Ticketek breach and continues to be targeted with attempted brute force attacks).
These emails are low sophistication and relatively easy to spot. Some giveaways:
The 0 instead of an O in ATO.
The email address
The email header “myG0v”
However, there are apparent attempts to make these look more legitimate with the use of a “reference number”.
In April 2025 I received more myGov phishing emails, however they were now more sophisticated and looked more professional.
You can see in the below image that they have now expanded the campaign to provide more details, while still keeping it generic.
They have also ditched the hyperlink for a button.
Despite the effort to make it more sophisticated the email addresses used still give them away. So does the overall generic nature of the emails.
Both websites are confirmed as phishing sites by the URL checker from NordVPN link checker. They are both also flagged by security vendors on Virustotal.
Thankfully all these emails have been sent directly to my Outlook junk inbox - which is a good first line of defence.
I am sharing this story to highlight that these events are common place and sadly it is difficult to avoid exposure. I am also keen to let people know that even if you think you were involved in a high-profile data breach to change your passwords and when possible get MFA.
You can’t stop getting exposed in a data breach but you can take steps to give yourself the best defensive posture.
IOCs
I am including all the IOCs I could collect relating to all of the above. I have done limited analysis on the following.
Emails
463179@llsinterpreters(.)com
471826@llsinterpreters(.)com
402018@llsinterpreters(.)com
ara453242@llsinterpreters(.)com
razbor@drustvo-razbor(.)hr
e.tsoneva@ilianci(.)com
contact@belezatop(.)shop
Website links
jdjrksjagdraw(.)sbs/funds
myeftserve(.)de/rss
snip(.)ly/iatnoa
snip(.)lyduyb2
myservsportal(.)de/support
simplifyincomuaccess(.)de/a