This report will provide insights into notable events that have happened in more recent months and provide two cybertrackers, one (#30) is the update of the recurring cybertracker that has covered the Russia-Ukraine war since February 2022 and the other (#29) is an ‘inactive’ cybertracker - covering all the hacktivist groups no longer active in the conflict as it is a considerable number since I provided a mid-2024 update.
TLDR
Russia-Ukraine war hacktivist activity continues, but groups have dropped from over 130 active down to 80.
Daily attacks against Russia or for Russia continue daily, with DDoS still the main attack type.
Claimed attacks against Operational Technology and the claimed use of ransomware have increased since mid-2024.
Doxing remains popular when targeting Ukraine military and government officials.
The line is blurred between information operations and hacktivist activity.
The pro-Russian hacktivist civil and the Telegram purge have disrupted their operations.
Pro-Ukraine groups, like IT Army Ukraine maintain persistent activity.
The ‘convergence’ between pro-Russian and pro-Palestine hacktivists continues.
Russia-Ukraine War Cybertracker Update
Since the early hours of February 22, 2022 I have been tracking and monitoring hacktivist groups engaged in a “Cyberwar” between Russia and Ukraine. What started as a means of understanding what felt like a new type of activity in the cyber landscape has resulted in a daily obsession three years on. (See my X account if you want to see silly amounts of Hacktivist posting)
While hacktivist activity does not maybe get the attention it deserves by the cyber community it still demands attention. It continues to blur the lines between hacking and information operations and remains a loud and persistent presence in the cyber threat landscape. What we see now in 2025 is an appetite for hacktivist groups to claim ransomware attacks, claim attacks on operational technology and claim significant data breach’s. Is the bite as bad as the bark? What I would ask you is this:
In an age of risk aversion, high legislative oversight and immense reputational pressures for digital organizations - does a cyber attack have to be successful? Or, is the claim enough to disrupt and degrade and deny?
I will leave you with that as we move onto the latest Cybertracker - which is remarkably the 30th edition. (Not bad for a meme farmer with a 10 year old laptop)
Overall, there has been a significant reduction in active hacktivist groups engages in activities related to the Russia-Ukraine war. Dropping from over 130 in July 2024, to 80 in early 2025. However, there are still new groups commencing operations and some of the original groups from both sides remain steadfast in their consistent operations. The two stand-outs are the IT Army Ukraine and Noname057(16), two groups who both use crowd-sourced members to conduct their DDoS attacks.
It seems that regardless of any potential peace deals that geopolitcally motivated hacktivism is likely here to stay into the medium term.
Timeline of “Cyberwar”
While the term “Cyberwar” has become something of an inside joke for cyber security professionals since its overuse and saturation with little to no clear evidence. It has merit in being used in regards to hacktivist activity, in as far as saying that it is an enabling function - yet, unlike its brothers and sisters in fields such as influence and information operations, hacktivism has clearly and overtly defined rivals who are often geographically disparate. These rivals pit themselves against not only their rivals countries networks, but also each other in an arm-wrestle of control of the cyber and information space. While this is not a genuine “Cyberwar” at present geopolitically motivated hacktivist groups might be as close as we get.
This timeline provides some of the most notable events that have taken place over the past three years - For a comprehensive overview of the hacktivist landscape of the Russia-Ukraine war keep an eye out for my complete book (if I ever write it).
Notable events
The following are some of the most notable events that have taken place in the Russia-Ukraine hacktivist space.
Noname057(16) Remains at the Top
Out of all the pro-Russian hacktivist groups to come and go, including the most infamous in Killnet and the most linked to Russian authorities, Cyber Army Russia Reborn, Noname057(16) has remained the most consistent and persistent. With daily DDoS attacks taking place with the support of its DDoS crowd-sourced tool DDoSia. Where other groups like Anonymous Sudan have emerged in a blaze of glory with paid-for-botnets only to vanish once again, Noname057(16) remains active with its crowd-sourced DDoS option. Even a shut-down of the main Telegram account has not slowed the group.
Pro-Russian Hacktivist Civil War
In mid to late 2023 there was a hacktivist ‘civil war’ this was largely fought out between two hacktivist personalities within the Russian ecosystem, Killmilk, creator of Killnet and Julia, the leader of the Cyber Army Russia Reborn.
Killmilk ended up allegedly moving to work with Beregini.
Killnet which was largely defunct was fully shutdown and the Telegram accounts sold.
Many pro-Russian hacktivist groups started to operate under the influence of Cyber Army Russia Reborn.
Former Killmilk allies continued to target Cyber Army Russia Reborn leadership as recently as February 2025 with Raty (former leader of Anonymous Russia) calling out the leader of Cyber Army Russia Reborn for running Z-Pentest.
Convergence takes place between Pro-Russian and Pro-Palestine Hacktivists
During the past six months a convergence has taken place between pro-Russian and pro-Palestine hacktivist groups - this convergence has resulted in targeting overlap and overt declarations of support, with pro-Palestine hacktivists increasing their attacks on Ukraine and Europe and pro-Russian hacktivists targeting Israel.
While overlap and team-ups have taken place sporadically, the creation of several alliances such as the Holy League under the leadership of Tito on the pro-Palestine side and Usersec1 on the pro-Russian hacktivist side has resulted in sustained teamups. Notably, Noname057(16) has maintained strong alliances with several pro-Palestine groups such as Alixsec.
While many who follow the multi-faceted hacktivist landscape might think that convergence of motivations is a recent event with the plethora of new allies that Noname047(16) has drawn from pro-Palestine circles. But, the original convergence took place in 2023 when Team 1919 and Team_insane_Pakistan teamed up with Usersec as part of the Usersec Collective.
This has continued to evolve to the point that two prominent figures have instigated the majority of convergence being:
Usersecc or Usersec1 - The creator of Usersec, the Usersec Collective and the Holy League. Largely is focused on a mix of geopolitically and financially motivated hacktivist activity and is a Pro-Russian operator.
TiTo - Tito is the creator of 7 October Alliance and possibly hackforce, Holy League and the Cyber Islamic Alliance. Tito is a pro-Palestine hacktivist.
Outside of these two main actors there has been efforts by firstly Cyber Army Russia Reborn and then by Noname057(16) to cross-campaign with pro-Palestine hacktivists. Which has resulted in attacks by pro-Palestine hacktivists group on pro-Russian targets and Noname057(16) targeting Israel to support them.
Noname057(16) Alliances
The following are the Alliances that Noname057(16) has created with both pro-Russian and pro-Palestine hacktivist groups. Noname057(16), up until September 2023 had not joined an alliance. However, this was also a possible period of change for the group - which may have started to get influence from Cyber Army Russia Reborn at this time (low confidence).
2024:
Alliance with Azzasec. Pro-Russian group from Italy.
Alliance with BAP. French hacktivist group.
Alliance with Cybervolk. Pro-Palestine group.
Alliance with 7 October Union. Pro-Palestine collective created by Tito.
Alliance with Hacker Council. Pro-Russian group.
Alliance with Alixsec. Pro-Palestine group.
Alliance with the Holy League.
Alliance with the Moroccan Soldiers. A pro-Palestine group.
Alliance with Al Ahad. A pro-Palestine group.
Alliance with Red Eagle Crew. A pro-Palestine group.
Alliance with pro-Palestine.
Alliance with Liquid Blood. A pro-Russian group.
Alliance with Z-Pentest. Declared this with Cyber Army Russia Reborn (September 27,2024)
Alliance with VoltActivist. Pro-Russian group.
Alliance with Sylhet Gang. Pro-Palestine group.
Alliance with Radnet. Pro-Palestine group.
Alliance with Evil Morocco. Pro-Palestine group.
Alliance with Alligator Black Hat. Pro-Palestine group.
Alliance with Indohaxsec. Pro-Palestine group.
Alliance with Team Arxu.
Alliance with Fredens of Security. Pro-Russian group.
Alliance with Kurtlarcyberlab. Pro-Palestine group.
Alliance with Mr. Hamza. Pro-Palestine group.
Alliance with Esteem Restoration Eagle. Pro-Palestine group.
Alliance with Fighter Blackhat Cyber Crime. Pro-Palestine group.
2025:
Alliance with Wolf Cyber Army. Pro-Palestine group.
Alliance with New Republic Coalition
Alliance with Sector16. Pro-Russian group.
Alliance with French Hackers Squad.
Alliance with Team Spider-X.
Alliance with Black-hat Zombies. Pro-Palestine group.
Alliance with Keymous. Pro-Palestine group.
Alliance with Mafiaowners.
The Great Purge
In late 2024 and early 2025 a great purge of hacktivists accounts on Telegram took place and this continues to today in a lesser extent. It remains unclear if this was French authorities after the arrest of Telegram CEO Durov or, if it was the use of several botnet services who offered to target Telegram pages for payment. Regardless of the source, the take-downs have caused considerable disruption and in the event of several groups - have seen them not return at all. The following is a cybertracker of the hacktivist groups from the Russia-Ukraine war who have been shutdown and not returned. Others have been taken down but continue to return, such as Noname057(16) and Overflame.
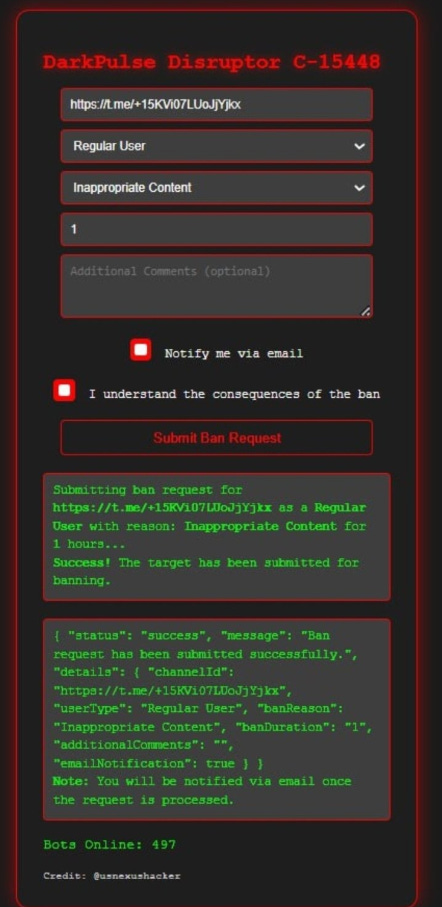
Darkpulse is one claimed paid-for-botnet which has been used to take-down Telegram pages.
Cybertracker #29 - Inactive groups Since July 2024.
Since the 28th addition of the Cybertracker in July 2024 there has been a large number of groups that have become inactive. I felt it would be best to capture them all into their own tracker. Most notably is the shutdown of Cyber Army Russia Reborn. But just as interesting is that at least half of the pro-Russian groups have come and gone between July 2024 and February 2025 - highlighting the dynamic and fluid nature of the hacktivist landscape
Cyber Army Russia Reborn down but not out?
Cyber Army Russia Reborn was a victim of the purge and in late December 2024 their Telegram account was shut-down. It seemed at the time that the group would return quickly, especially considering its status as the unofficial ‘leader’ of a growing cadre of pro-Russian hacktivist groups. however, the group has still not returned.
It does look like however, like Z-Pentest may have been the group that has taken up the slack and in recent days the group has revealed that Julia the former head of Cyber Army Russia Reborn has joined them. That might explain why Z-Pentest has been conducting DDoS attacks - something they had not done previously
On 11 February 2025 Z-Pentest declared that Julia had joined their ranks. For additional context, the United States has sanctioned Julia the leader of Cyber Army Russia Reborn.
Its possible that Cyber Army Russia Reborn does not return as a Telegram group.
Pro-Ukraine groups continue operations
Pro-Ukraine hacktivist groups remain consistent throughout the conflict and these groups suffered less at the hands of the purge, possibly due to their smaller overall group numbers and smaller member bases. What has been noticeable is the tactical aspect of many pro-Ukraine hacktivist operations, even the most well-known, IT Army Ukraine has been conducting sustained crowd-sourced DDoS attacks on targets in support of Ukraine military operations. For instance, the group targets telecommunications networks in occupied areas in attempts to likely diminish Russian military C2.
Doxing remains a popular and significant tool for some Pro-Russian groups.
Pro-Russian groups like JokerDPR and Beregini continue to dox Ukraine military members and also foreign fighters in Ukraine. This type of doxing can have significant real-world implications and is possibly placing individuals at risk in the battlespace. The tactic of doxing is also being conducted by pro-Ukraine groups.
Beregini and JokerDPR also continue to post claimed leaked documents that expose claimed corruption and misconduct by Ukraine officials and military members. This highlights the information operations aspect that has come to be so prevalent in the Russia-Ukraine War hacktivist landscape.
DDoS remains King, but Ransomware and Operational Technology increased.
In the past year there has been a notable increased in hacktivist groups looking to leverage Ransomware as a means of network disruption. For the most part this highlights the continued increase in financially-motivated hacktivist groups. There has also been an increase in hacktivist groups claiming to conduct attacks on internet facing operational technology.
In particular this has increased by pro-Russian groups like Z-Pentest and Sector16, these claimed attacks appear to have mixed levels of success but they are indicative of the shift in the hacktivist landscape as groups seek out more destructive attacks beyond DDoS.
Outlook
The hacktivist landscape of the Russia-Ukraine war will remain an active part of the cyber landscape. Some of the groups involved are so well-established now that they would find it hard to shut up shop and go home, instead they could pivot to new causes driven by geopolitical flashpoints. Or, they will continue to attack Russia or Europe respectively. Overall, geopolitical hacktivism is likely here to stay and organizations and governments need to remain aware that geopolitical events now trigger cyber responses in the form of DDoS, Ransomware, defacements, data leaks, Doxing and operational technology targeting.









Thx! (Source)
https://www-ccinfo-nl.translate.goog/menu-onderwijs-ontwikkeling/cybercrime/cyberoorlog/2348859_nieuwe-dimensies-van-cyberactivisme-in-de-oorlog-tussen-rusland-en-oekraine?_x_tr_sl=nl&_x_tr_tl=en&_x_tr_hl=nl&_x_tr_pto=wapp