The Microsoft DDoS attacks - Hacktivism or Vendetta?
Anonymous Sudan and Zarya Legion
TLDR
Anonymous Sudan’s most high-profile DDoS attack was against Microsoft in June 2023, below we review insights that reveal they may have had help from another pro-Russian hacktivist group, Zarya Legion.
Zarya Legion may have been linked to Zloader botnet. Microsoft shut-down Zloader botnet in April 2022 - Zarya Legion spent a year possibly rebuilding their botnet for a revenge attack in June 2023.
Zarya Legion unlike every other pro-Russian group values discretion and on several occasions have backtracked when accused of actions instead of bragging like most others.
Zarya Legion has also placed more privacy controls on their telegram page, blocking screenshots - they appear to only be communicating with their followers instead of looking for attention from the West like other groups.
Anonymous Sudan possibly leveraged a botnet that Zarya Legion was running to target Microsoft.
Many argue that Anonymous Sudan would struggle to achieve such an attack without paying large sums for botnet access - what if they were supplied the capability to conduct the attacks?
Zarya Legion on several occasions made reference to a relationship with Russian intelligence services.
Summary
Anonymous Sudan started operating in January 2023 and since then has quickly captured the interest and curiosity of threat researchers and the global media, thanks in large part to their successful DDoS attacks on Microsoft in June 2023.
As someone who has been tracking and monitoring the cyber component of the Russia-Ukraine War since February 2022 I have a decent understanding of the hacktivist landscape. What has stood out about Anonymous Sudan is the fascination by researchers, maybe even more so than for Killnet, this might center mostly around the narrative driven by Anonymous Sudan themselves that they are Sudanese hacktivists. In contrast a large part of the community believe they are Russian state-supported, realistically they could be both or neither of those things.
So, come along for a ride as we explore this new angle into Anonymous Sudan and their successful DDoS attacks on Microsoft in June 2023.
Disclaimer
This report looks at the subject material from the perspective of intent and the opinions of the threat actors involved, where possible I have tried to correlate claims.
This report will likely raise more questions than answers, if you have any insights or challenges to its contents please reach out.
Crowd-sourced intelligence with a diversity of thought will always beat siloed echo chambers.
Report
The following report will outline why it is possible that Zarya Legion, a group who openly claims to have engaged with Russian Intelligence services may have helped Anonymous Sudan target Microsoft and why, it might even have been an act of revenge.
Who is Zarya Legion?
Zarya Legion started their telegram account in the early period of the Russia-Ukraine war, on 3 March 2022. They state their specialty is to ‘gather information’. I will point out early that unlike all other pro-Russian hacktivist telegram groups, Zarya legion locks the page to avoid screen shots – in that regard they appear more interested in showcasing to their supporter base then having their exploits shared with ‘Russophobic’ countries. However, most of their comms are in English.
Now, for many this might cause some confusion - let me clarify that there are two Zarya groups who both state they have links to Killnet. I will differentiate them by calling one Zarya and one Zarya Legion. (Both have been added to the cybertracker in different versions) Where as Zarya was a unit from the original Killnet, Zarya Legion is a group that claims to support Killnet.
Zarya was one of the original special forces groups of Killnet back in March 2022 and is arguably the most capable of any Killnet group, conducting a series of alleged breach and leak attacks against Ukraine. The group has also conducted multiple interviews with Russian media and welcomed Western attention. They sought attention and notoriety like all Killnet collective members. Which is a key point of difference between the notably ‘shy’ Zarya Legion and the overt Zarya.
Zarya confirmed in April 2023 that they are separate to Zarya legion. They also importantly recognize Zarya Legion as a legitimate group. This is important as establishing the legitimacy of not well-documented groups can be difficult.
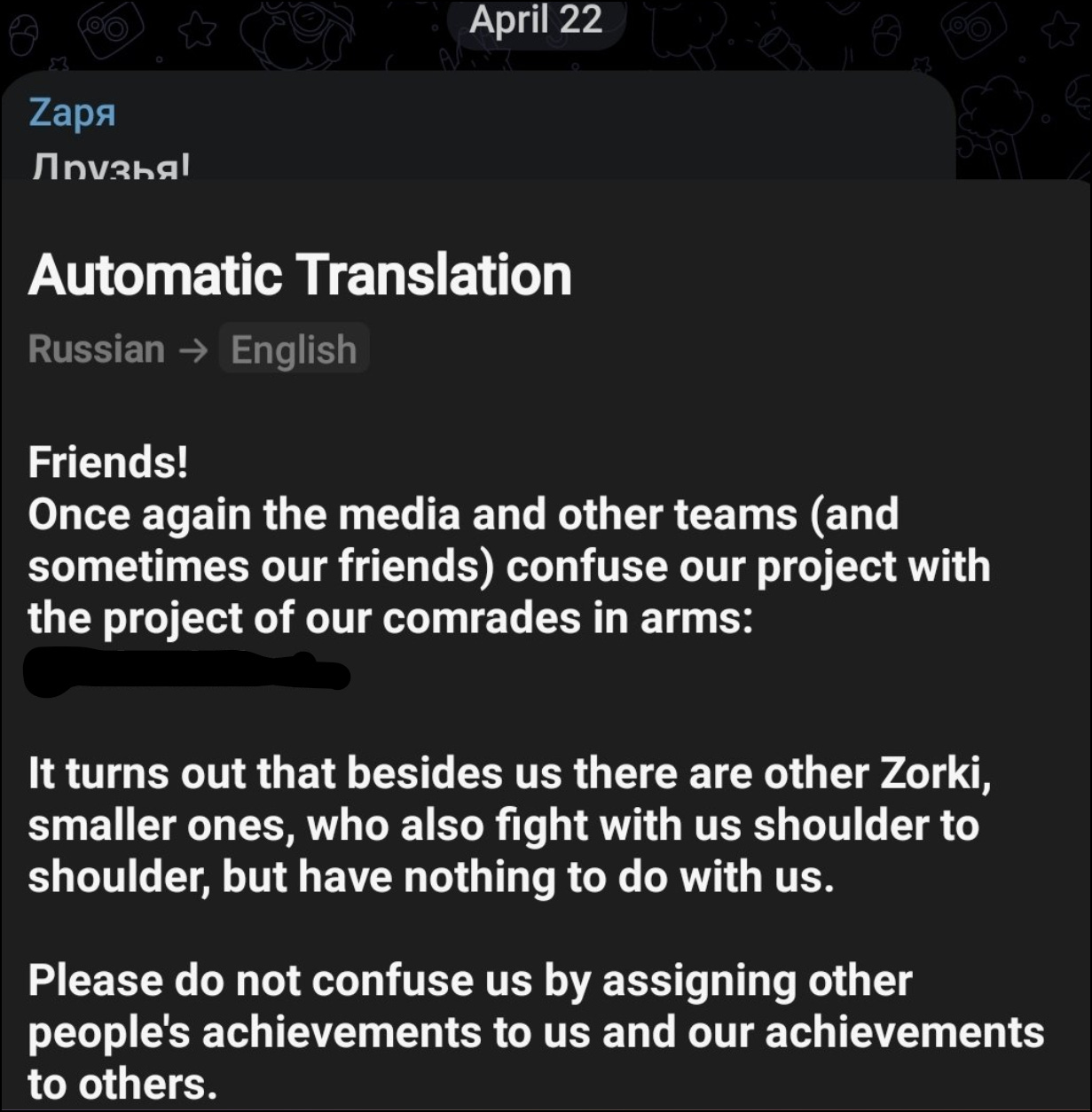
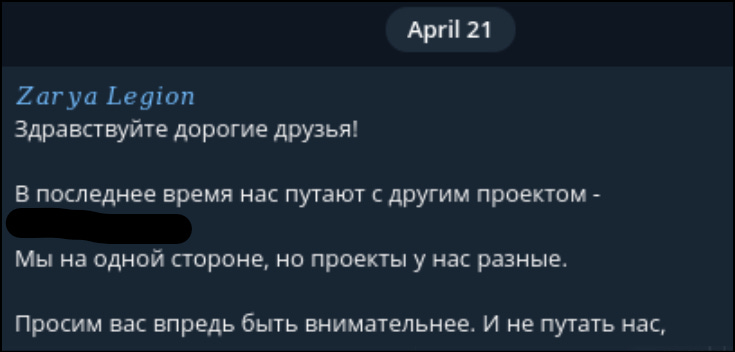
Zarya Legion also pointed out in April 2023 that they are confused with Zarya.
Translation: Hello dear friends! Lately we have been confused with another project Zarya. We are on the same side, but our projects are different. We ask you to be more careful in the future and don’t confuse us with other teams.
What happened in April 2023 that had both Zarya and Zarya Legion want to clarify who is who? It was revealed in leaked US government documents by the New York Times that a Russian intelligence officer had been informed by ‘Zarya’ that they had hacked a Canadian pipeline and could manipulate the system.
Analyst Note:
Neither group accepts responsibility for these claims. Zarya would normally brag about this kind of attack - Zarya Legion on the other hand would not advertise it openly.
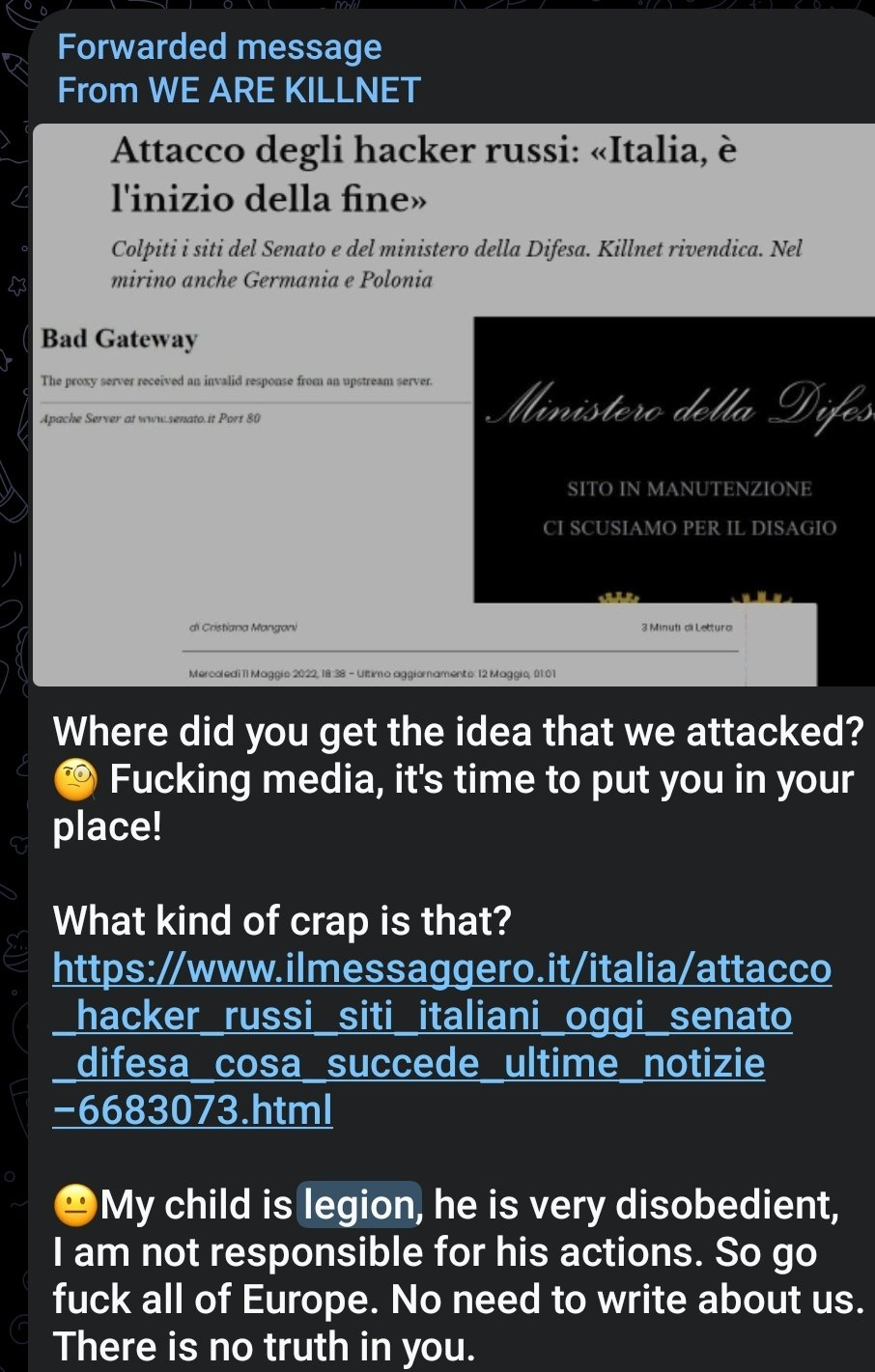
Now we have touched on that, let’s get into Zarya Legion. The only way we can confirm that Zarya Legion was actually related to Killnet (outside of Zarya Legion stating it) was in April 2022 when Killnet gets angry that they are being blamed for a Zarya Legion attack in Italian news. ( Zarya Legion did not claim to conduct the attack directly, but does recognize it after the event)
Analyst Note
While Killnet does have the Legion group, in this scenario they appear to be talking about Zarya Legion - who appears to be a support group that was not created by Killnet.
As you can see Killnet was not as happy about claiming any and all attacks as much when they started as they do now. To clarify that Killnet is talking about Zarya Legion and not Zarya - a review of Zarya activities shows they have never mentioned Italy. While Zarya Legion posted the following after the Killnet post.
Zarya Legion runs into trouble - April 2022
Zarya Legion started on Telegram in March 2022, but by April 2022 they suffer some issues. As you will see below they discuss Microsoft and then complain about having their botnets destroyed. At this point they stop posting and do not post again until July 2022. This is a long period of silence for most pro-Russian hacktivist groups.
While correlation does not equal causation - the timing of the posts of Zarya Legion are directly after Microsoft revealed publicly that they had dismantled the Zloader botnet. It is difficult to confirm if the members of Zarya Legion were involved with Zloader botnet, but it is a fascinating point of coincidence. As you will see below, hate towards Microsoft is a constant theme for Zarya Legion.
Zarya Legion then continues with more months of sporadic activity - possibly while they fix whatever happened to their botnet.
This sporadic activity then continues until February 2023. As you can see they once again claim ‘to be back soon’ then vanish for three months.
They do provide a short video which is notably in Russian, compared to almost all their written comms which are in English. I sought out one of the finest translators I know, who said the great majority of the video is inaudible.
After they post the video they shift into a period of promotion of their botnet. They don’t previously mention much about botnets other than it getting shutdown almost a year before.
Then, on February 26 they once again mention Microsoft, there is a recurring theme since the announcement of the botnet shutdown in 2022 that they have issues with Microsoft.
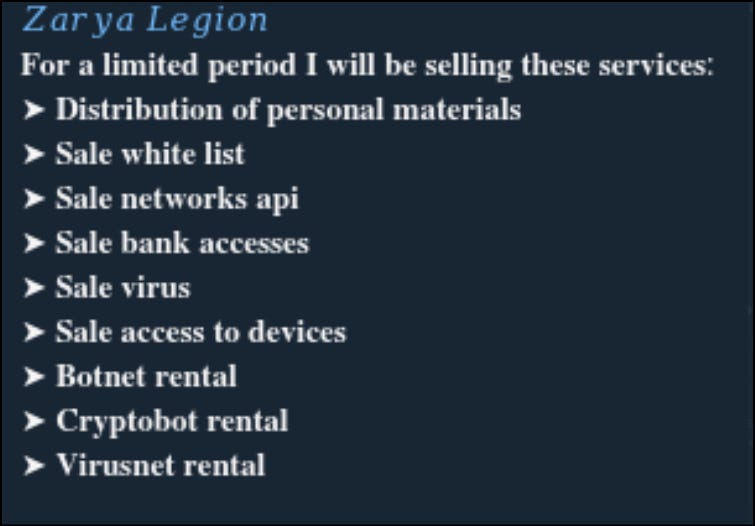
For the first time Zarya Legion now offers their services for payment, really the usual offerings for most groups. What it might indicate is that after a long period they have been able to reestablish their product to now sell to customers.
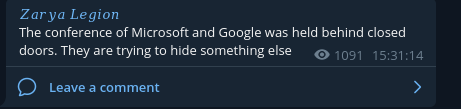
Oh, they once again mention Microsoft - As I said above the theme of hatred towards Microsoft is consistent throughout the groups postings.
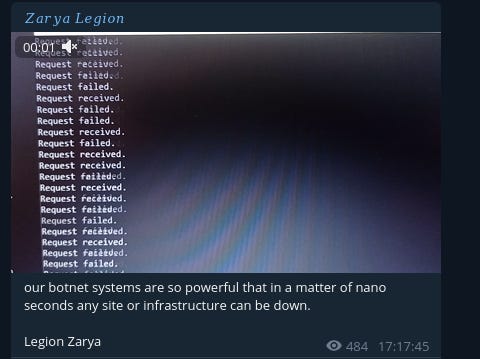
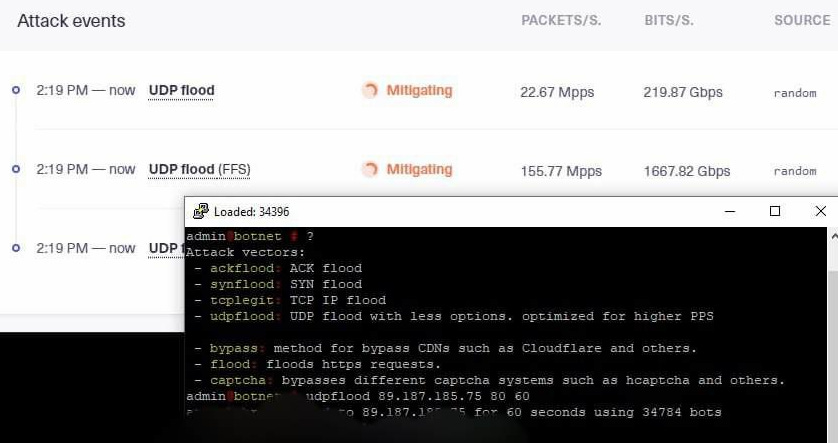
On March 8 Zarya Legion provides a screenshot of their botnet in action.
They provide a range of services, similar to the type mentioned by Microsoft as being used in the DDoS attacks by Anonymous Sudan. This also shows that the botnet in use has at least 34784 bots at this time.
They then conduct a series of DDoS attacks on various government websites (unclear if any where successful) this is likely to showcase the ability of their services.
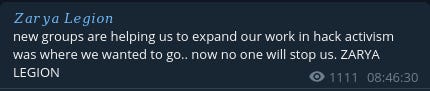
Then on March 21 they announce:
While they on occasion mention their support for Killnet they have not shared or cross-posted Killnet activities, which is a common practice for groups linked to Killnet.
Zarya Legion then increases their claimed DDoS attacks and for the first time since the page was created in early 2022 they are regularly posting and are very active.
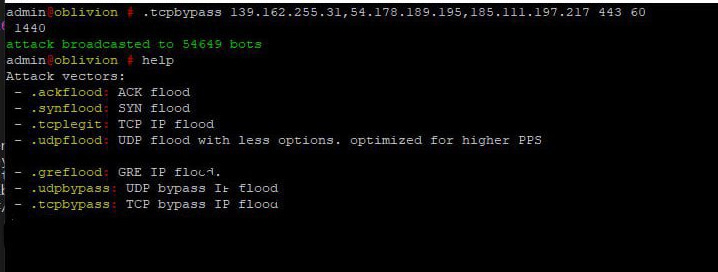
On April 7 2023 they provide another screenshot related to their botnet:
At this time we can see that they have increased the bots in their botnet to at least 54649. This increase in capability might be why the sudden increase of activity on the groups telegram.
All this new activity once again comes to a stop in late April 2023 when the revelation is made via the leaked US documents that a ‘Zarya’ hacktivist group has attempted to sell Canadian company access to possible Russian intelligence members. Remember neither Zarya and Zarya Legion claim this.
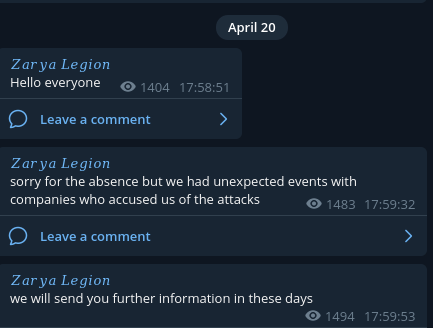
It isn’t until April 20 that Zarya Legion posts again referencing the release of the New York Times article which was on April 13.
This is also the same time that they clarify they are not Zarya but are instead a different group.
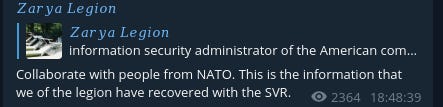
After this event they release a heap of NATO and US government documents - which all look unclassified and are possibly from an earlier breach. They also interestingly post information and make, for the second time a claim that they are working with or sharing information with the Russian intelligence services.
Remember, this is a smaller and private telegram page than all other pro-Russian hacktivist groups.
Zarya Legion and Anonymous Sudan
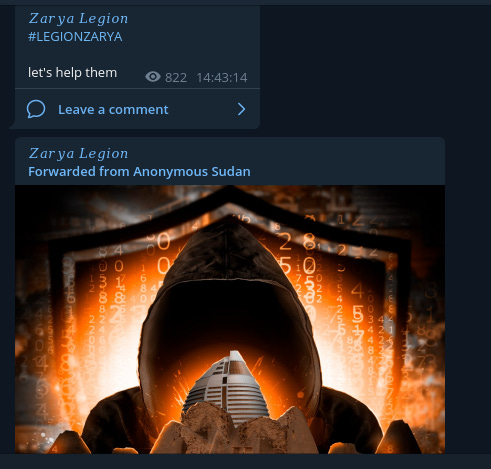
On 25 April 2023 Zarya Legion posts ‘let’s help them’ they then follow that post up by forwarding a post from Anonymous Sudan. Up until this point Zarya Legion had not shared or forwarded any other attacks relating to any other pro-Russian groups, including for Killnet.
As you will recall just above on March 21 they reference that they are planning to start working with hacktivist groups, now less than a month later Anonymous Sudan is being mentioned.
Analyst note:
From April until July Anonymous Sudan conducted its most impactful DDoS attacks, with confirmed impact against SAS airlines, allegedly the Israel Iron dome and of course Microsoft. All these attacks took place with possible support of Zarya Legion.
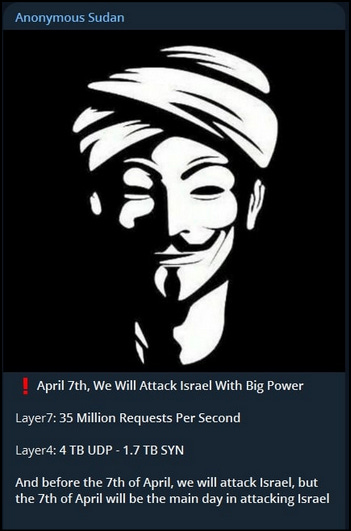
On April 7 Anonymous Sudan brags about the capability they can leverage against Israel - this comes after the March 21 Zarya Legion announcement that they would help Anonymous Sudan.
This does not confirm that Anonymous Sudan is using the Zarya Legion botnet.
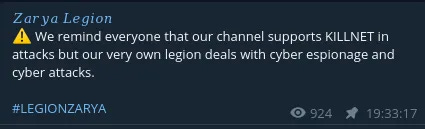
Zarya Legion then randomly clarifies that they support Killnet in attacks but conduct separate operations - this would explain why they don’t cross-promote or declare they are joining attacks. Once again Zarya Legion wants to distance themselves from public exposure and highlight they operate in the shadows.
They have little interest in being mentioned by Western media unlike other groups who crave the exposure.
On April 30 Zarya Legion discusses testing their botnet to make sure it works during attacks. Despite the screenshot being hard to read, there is one part which provides capabilities - assuming this means bots in the botnet then the number appears to be 63487 - which would suggest the botnet has been growing.
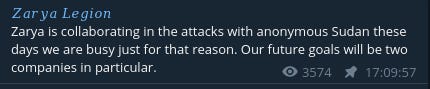
Zarya Legion announced on April 30 that they were continuing to collaborate with Anonymous Sudan and that two companies would be targeted in particular, these likely being Microsoft along with possibly UPS.
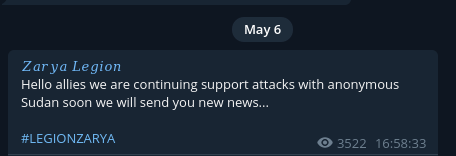
Zarya Legion repeats that they are supporting Anonymous Sudan attacks, the wording is worth noting, they always state they support Anonymous Sudan or support Killnet, not that they are conducting attacks for them.
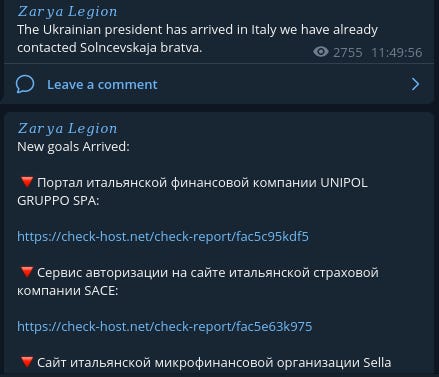
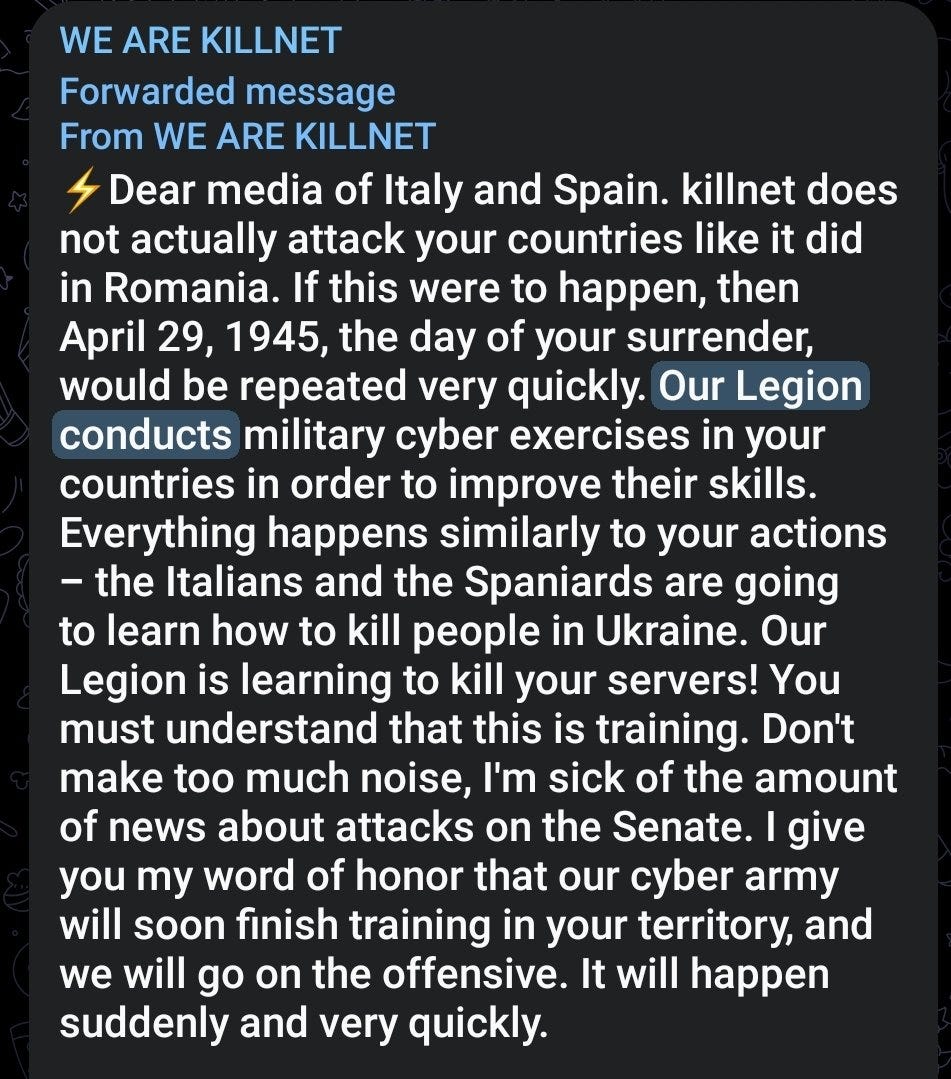
However, this appears to change round 11/12 May when Zarya Legion conducts DDoS attacks against Italy, Spain and several other countries. Using a trip made by President Zelensky to those countries as a cover to test their new capability.
It was reported at the time in the media that Killnet claimed the attacks, however they explain that it was testing by their Legion. As I mentioned above when they mention ‘Legion’ is appears to reference Zarya Legion.
Some key takeaways from this post:
This is forwarded from a private ‘We are Killnet’ account to the public group, this is ultra rare and might be the only case that a private account has posted into that group.
Killnet does not claim the attacks as they do others, instead they speak of their ‘Legion’ this is the same way they referenced Zarya Legion in 2022.
They call this a training exercise to improve their skills - according to Bleeping computer, the Italian CERT stated the attacks were using a ‘Slow HTTP’ attack technique. This is an attack that Microsoft said was used against them in June- that attack would take place a month from these attacks.
It is possible that Zarya Legion was training with a new ‘Slow HTTP’ attack technique and Killnet was keen to clarify that?
Zarya Legion then continues to conduct DDoS attacks which are not declared by any other pro-Russian hacktivist group up until around 25 May when they announce.
The Microsoft Attacks
Up to this point we have had Zarya Legion possibly have a botnet disrupted by Microsoft in April 2022. After that possible incident Zarya Legion continues to vent frustration towards Microsoft. Then after over a year, in April 2023 they get a botnet that appears to be able to provide DDoS attacks. Not only this but its possible they were testing out capabilities with attacks on Italy and other sites in late May 2023.
They also mention they are working with Anonymous Sudan to target two organizations. This all leads, from what I can see to the attacks on Microsoft in June 2023.
I think the story has been well covered by now - but some quick points:
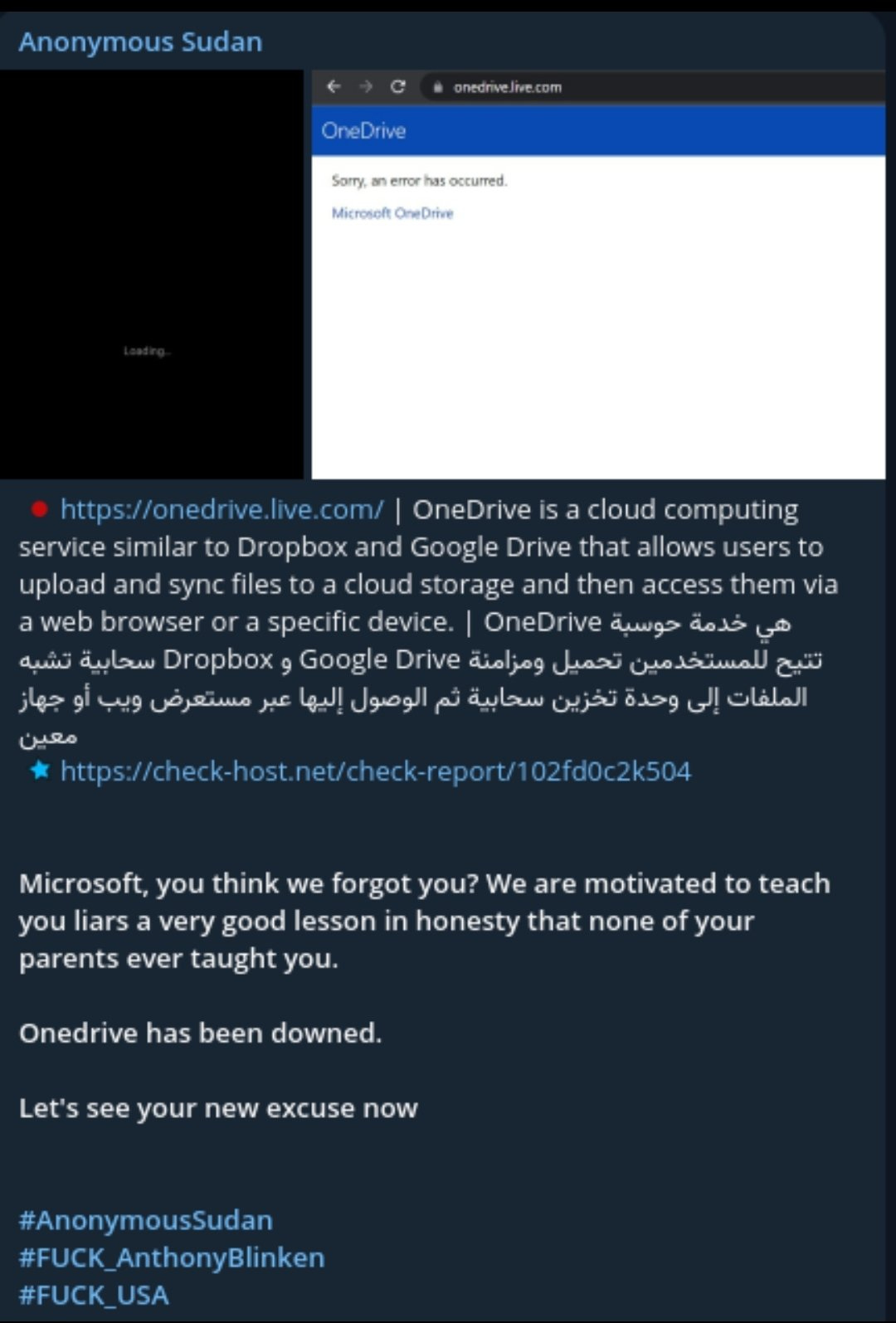
6 June Anonymous Sudan starts to target Microsoft with DDoS attacks.
Thousands of US based customers are impacted.
They continue the attacks until at least 10 June.
The narrative by Anonymous Sudan was overtly personal towards Microsoft, which in isolation doesn’t seem like much.
At the time Microsoft had no obvious actions that would trigger a geopolitical or religious response, which Anonymous Sudan often claims to use as motivation.
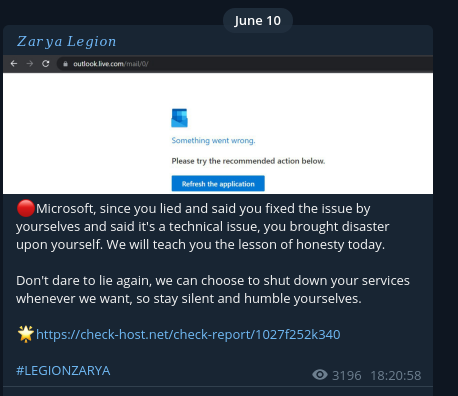
Zarya Legion didn’t share any Anonymous Sudan posts about the Microsoft attacks - but, they did post their own separate post
Anonymous Sudan posted something similar but with different wording. This would mark the first time that Zarya Legion would post a statement like this - It is unclear if they conducted this attack on Microsoft themselves or if they simply supported Anonymous Sudan. Below is the post that Anonymous Sudan put up relating to Microsoft lying about the attacks. You will note the differences.
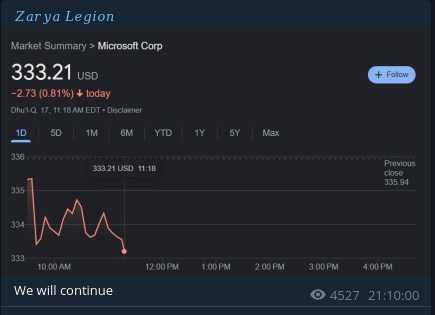
Another thing that Zarya Legion posted was the impact of the attacks to Microsoft’s share price, again highlighting this had more a revenge vibe about it.
Its as if Zarya Legion really wanted to make Microsoft suffer, for no really obvious geopolitical reasons. Yes, Microsoft has been a strong supporter of Ukraine, but nothing recent was announced around the time of the attack.
After this post Zarya Legion post one more time on 16 June then go offline until August. When they return on 15 August they post about taking down a crypto exchange and then exposing Twitter credentials of people who used the exchange. Since then the telegram group has had no activity.
Finally, it is worth noting that Anonymous Sudan did try and attack Microsoft again in July - but this time they openly declared they were using Skynet and Godzilla botnet - they had little success that time.
Is this because Zarya Legion stopped providing them with capability now that Microsoft has been impacted?
Notably, Two targets, SAS and Microsoft were targeted outside of possible Zarya Legion support but were not as successful.
SAS was targeted in February with less impact than during the May attacks.
Anonymous Sudan tried to target Microsoft again in July but with less success.
Thoughts on the Microsoft Attacks
One overarching thought about the Microsoft attacks was why them? There was nothing notable in the media at the time about Microsoft that would trigger Anonymous Sudan to attack, sure Microsoft supports Ukraine, but there was no clear trigger point that would provide the justification Anonymous Sudan often claims. Is that because it was an act of revenge by the operators of Zarya Legion? Or, was it simply that they had the opportunity to target a big US company?
The fact that they were able to impact Microsoft makes it a fascinating event and one that I am sure people will explore and debate for sometime. I hope this report inspires debate and further research - Hopefully not a series of DDoS attacks.